How NIST’s New PQC Algorithms Impact You


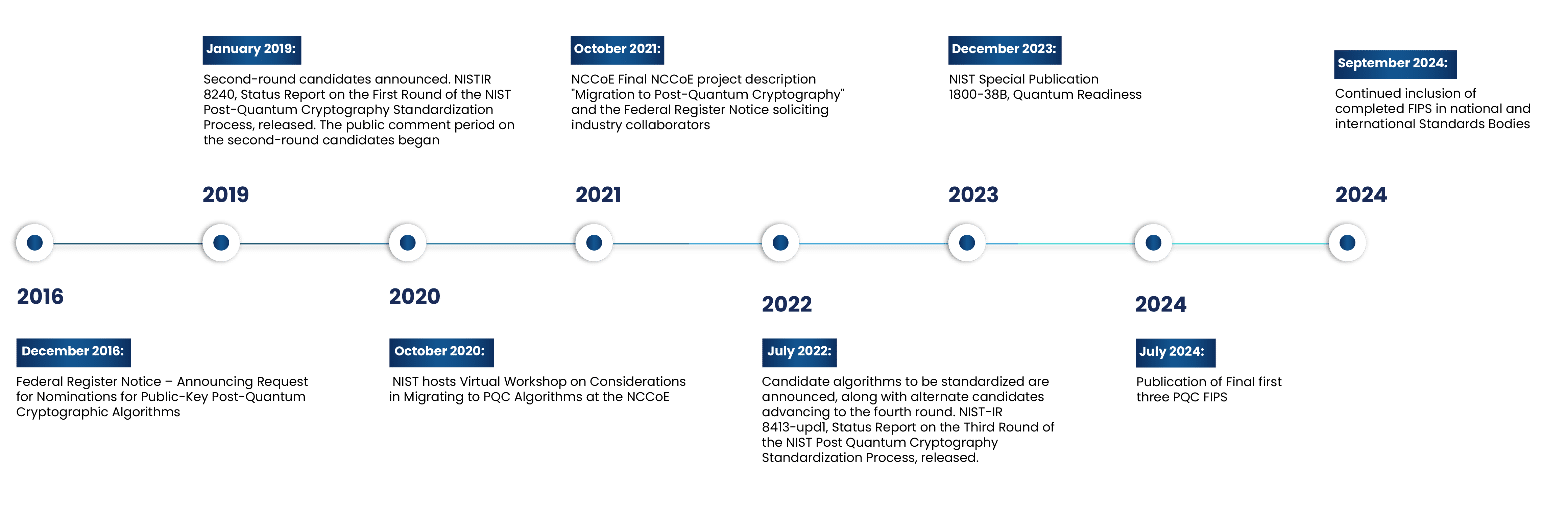
The National Institute of Standards and Technology (NIST) has officially released the first three post-quantum cryptographic algorithms. The three algorithms are ML-KEM, ML-DSA, and SLH-DSA. Earlier, these algorithms were known as CRYSTALS-Kyber, CRYSTALS-Dilithium, and SPHINCS+. There is also a signature algorithm FN-DSA proposed to be issued as a draft standard at the end of the year, which was earlier known as Falcon.
We have recently received a lot of queries, including can an organization start implementing these PQC-safe algorithms? Are these the finalized algorithms? Are these the ultimate cryptographic algorithms that will secure our systems from a quantum attack?
The finalization of these algorithms means that organizations can now start implementing PQC-safe algorithms into their Public Key Infrastructure (PKI) to help ensure that systems that rely on secure digital identities and the exchange of encrypted data are safe from being broken by quantum computers.
Many organizations have already started developing strategies and roadmaps to migrate to PQC algorithms, and these PQC algorithm releases effectively create a starting point toward PQC readiness. But the truth is that organizations that are only just starting to think about migrating to the new standards are getting a late start in the race to secure the infrastructure that underpins their cryptographic assets.
Now, let’s talk a little more about the PQC Algorithms:
1. ML-KEM: FIPS 203 (Module-Lattice-based Key-Encapsulation Mechanism Standard)
ML-KEM provides a Key-Encapsulation Mechanism for sharing symmetric keys for general encryption. FIPS 203 states that it establishes a shared secret key (Symmetric key) between two users who communicate over a public network.
For more information, read In-Depth Overview of FIPS 203
2. ML-DSA: FIPS 204 (Module-Lattice-Based Digital Signature Standard)
ML-DSA is used to secure digital signatures. This standard outline specific details of algorithms used to generate and verify digital signatures, and “ML-DSA is considered secure, even against adversaries in possession of a large-scale quantum computer.”
The digital signature and the signed data are provided to the intended verifier. The verifying entity verifies the signature using the claimed signatory’s public key. Similar methods may be used to generate and verify signatures for stored and transmitted data.
For more information, read Understanding FIPS 204
3. SLH-DSA: FIPS 205 (Stateless Hash-Based Digital Signature Standard)
A stateless hash-based digital signature algorithm that is also used for data authentication and verification is described in FIPS 205.
For more information, read In-Depth Analysis of FIPS 205
| Type | FIPS Name | Current Specification Name | Initial Specification Name |
| KEM | FIPS-203 | ML-KEM | CRYSTALS-Kyber |
| Signature | FIPS-204 | SLH-DSA | CRYSTALS-Dilithium |
| Signature | FIPS-205 | SLH-DSA | Sphincs+ |
| Signature | FIPS-206 | FN-DSA | FALCON |
Those who haven’t started preparing for PQC readiness must understand the recommended next steps for PQC readiness.
The migration strategy depends on many factors, such as compliance requirements, business requirements, the need to be aligned with industry best practices, and more. However, let’s talk about the key points that will help an organization for a successful migration to PQC
Our detailed Quantum Threat Assessment service utilizes advanced cryptographic discovery to analyze and secure your cryptographic infrastructure.
The Post-Quantum Cryptographic Advisory Services offered by Encryption Consulting LLC help clients overcome the cybersecurity obstacles brought on by quantum computing. We offer perspectives on possible quantum hazards, steer the shift towards quantum cyber-preparedness, and align to Post-Quantum Cryptography (PQC) guidelines suggested by top organizations such as NIST. We assist companies in evaluating and updating their cryptographic infrastructure, so they are ready for the quantum age through proactive cryptographic discovery and strategic planning.