Understanding how code signing impacts your organization


The executable file that is being delivered is digitally signed when a developer code-signs their programme. Consumers of the programme consider the intact signature as evidence that the code has not been modified between the time it was transmitted and the time it was installed on the consumer’s device. This signature functions as a kind of “wax seal.” Code signing entails applying digital signatures to distribute files using public key encryption
Today, the internet is the primary means by which software is distributed, accessed, and used – almost every application on your computer was probably downloaded online. The widespread use of this media has also increased the risk of criminal activity.
For example, hackers and internet criminals may steal the executable file’s source code, add malware to it, and then make the software accessible for online discovery and distribution. Naturally, the malware would infect every user who downloaded and installed this file.
Code signing prevents this scenario from happening. Your operating system prevents the installation of any programme from moving forward without first verifying the presence of a code signing certificate when you download and install it. The user is informed if a certificate from a trusted vendor is missing at this point, they can decide whether or not to continue with the installation.
For Developer
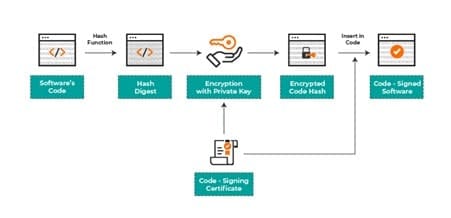
The creator must first create a special private key that may be used to encrypt the data. According to the theory behind public key cryptography, a private-public key pair is a collection of encryption techniques that can be used for encryption and decryption. After the key pair has been created, the public key is sent to a Certificate Authority (CA), a reputable organization that issues certificates.
The CA confirms the developer’s legitimacy before attaching their public key to a digitally signed certificate, the developer’s evidence that they are the rightful owner of the key. The developer who requested the certificate receives the public key and certificate back from the CA.
For Consumer
Before a programme is installed, most consumer operating systems are set up to check for the presence of a code-signing certificate. When an installation is requested, the OS first verifies the certificate’s validity before decrypting the digest using a public key from the CA.
An item (document, file, script, library, etc.) utilized during the software development process is referred to as an intermediate artefact. These artefacts should be signed throughout the development cycle to prevent modification by anybody other than the authorized creator.
Developers can modify a file or script in their development environment, code sign it, and then keep the signed artefact in their repository for future use. These intermediate artefacts’ code signature aids in preventing hackers from introducing undesirable components throughout the building process. Many diverse components are used in contemporary software development approaches.
A significant breach could occur if malware infiltrates any of these components. It is essential that your software development teams take this into consideration. Your software development teams must code sign all the intermediate artefacts they employ to create software as a result.
Carry out code integrity checks
Any code that developers check-in must be digitally signed using their signing key. To ensure that the final code published is unmodified, all developer signatures must be checked. The final build should be signed and released once all of these checks have been finished. A crucial step that helps ensure that the software update is free from tampering and secure for usage by your clients is verifying the integrity of the source code.
Store keys in a highly secure location
One of the biggest mistakes businesses make when it comes to key storage is keeping the keys on a hard drive, a developer’s personal computer, or built servers. This error can give attackers a broad window of opportunity to obtain your private keys and compromise several systems. Always keep your code signing keys very secure cryptographic areas, such as a FIPS 140-2 level 3 hardware security module, to prevent this danger (HSM). HSMs are exceedingly difficult to breach since they are tampering resistant. You can be guaranteed that no private keys are ever exported and that nobody else will ever have access to or use the code signing keys improperly.
Rotate keys
Sometimes, organizations tend to use the same key to sign releases across different product lines and businesses. This cannot be a good idea at all. All the releases you have signed with the code signing key run the risk of being hacked. Instead, it would be wise to alternate your keys on a regular basis. Additionally, utilize distinct and independent keys to sign various releases across DevOps teams.
A Code Signing certificate is essential for the user’s trust and to ensure that your source code is intact. Furthermore, it allows you to ensure that your application is not exposed to cyber-attacks. Increasing cyberattacks and a massive app market mean you must be ready on the security front.

March 12, 2025

February 24, 2025