Digital certificates play a crucial role in web security and public key infrastructure, ensuring secure internet communication. These certificates act like digital identifications that verify a website’s legitimacy. Now, consider a scenario where you try to access a website, but unknown to you, the certificate validating this site has been compromised. This oversight opens a back door for hackers to intercept your sensitive information.
To address such risks, every certificate has a finite validity period during which it is considered trusted. However, during this time, situations may arise where the owner or the Certification Authority that issued the certificate may declare it as untrusted. For example, if the private key of the certificate is compromised or if the owner of the certificate no longer controls the domain for which the certificate was issued, then the certificate becomes a liability.
In such a case, the untrusted certificate is revoked, and the certificate users are informed about the revocation. This is done by adding the given certificate to a Certificate Revocation List (CRL). A CRL is simply a blacklist managed by the CA that lists the certificates that should not be trusted and are no longer valid. Although these CRLs maintain trust in the PKI infrastructure, an expired CRL can present us with hidden risks and challenges that can undermine this trust.
Working of CRL
CRL is the only way for the PKI to know whether a certificate has been revoked before its expiry. While PKI provides a list of trusted users through issued certificates, it is also very important to know the ones who are no longer trustworthy. CRL serves this very purpose by listing the certificates revoked before expiry.
Steps Involved in CRL are as Follows:
-
Request Initiation
The entity that has been issued the certificate detects that the certificate needs to be revoked, which could be due to compromise, misuse, etc., and sends a revocation request to the issuing CA. This request typically includes the certificate serial number and the reason for revocation.
-
Revocation Request Process
Then, the CA verifies the authenticity of that revocation request, and once the request is validated, it marks the certificate as revoked in its internal records.
-
List Updating and Signing
After that, the CA adds the revoked certificates to the list and updates the CRL. The integrity of the revised CRL is then verified by having the CA’s private key sign it.
-
CRL Publication
The signed CRL is published and made available to the public and other entities that rely on the certificates issued by the CA. This is done through various methods, like publishing on a web server and distributing via LDAP.
-
CRL Distribution
Browsers, servers verify the status of certificates by periodically downloading the CRL from the specified location.
-
CRL Usage
Now when any browser or server encounters a certificate, it checks its serial number against the downloaded CRL. In case the certificate is found in the CRL, it is considered revoked.
How to View the Certificate’s Revocation Status
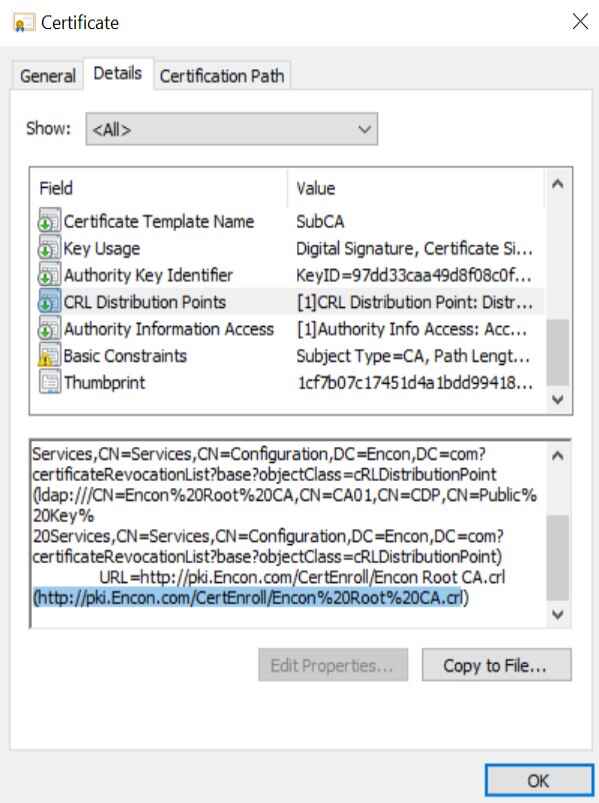
The CRL is made available by the Certification Authority at a specific distribution point, also available with the certificates.
If you have the digital certificate downloaded, then you can open it, or if it’s the certificate with a website, then click on the PADLOCK icon next to the URL and follow the given steps:
- Click on the Connection is Secure and then the Certificate is valid button.
- Go to the details section and scroll down to CRL Distribution Points (CDP).
- You will see one or more URLs pointing to the location where the CRLs are published.
- In the field value, copy the URL and paste it into the search bar.
- The browser will download the CRL file. You can access it to check the revocation list info.
Risks of an Expired CRL
Security Risks: Accepting a Revoked Certificate
If a CRL is outdated or expired, systems that are relying on it may not be aware of the recent revocation updates. This would mean that a compromised or an invalid certificate could be accepted by the systems trusting it, and would lead to a vulnerability waiting to be exploited by hackers.
Operational Risks: Service and Compliance Issues
Many of the applications and servers are hardened to always check for the CRL before accepting the certificate. Now, if the CRL has expired, these machines might just reject the certificates automatically, leading to outages and interruptions. Regulatory standards often mandate the use of an up-to-date CRL. Non-compliance with the standards might lead to financial losses to the organization.
Trust and Revenue Risks
If a server is unable to reliably verify the status of a digital certificate, it risks the trust in digital communication and leads to revenue losses for the organization, as users and systems can no longer be completely sure about the integrity of certificates.
Mitigating the Risks with CertSecure Manager
CertSecure Manager offers a PKI health view to pre-detect and monitor such failures. The following is a detailed explanation of how CertSecure Manager helps in resolving these complications:
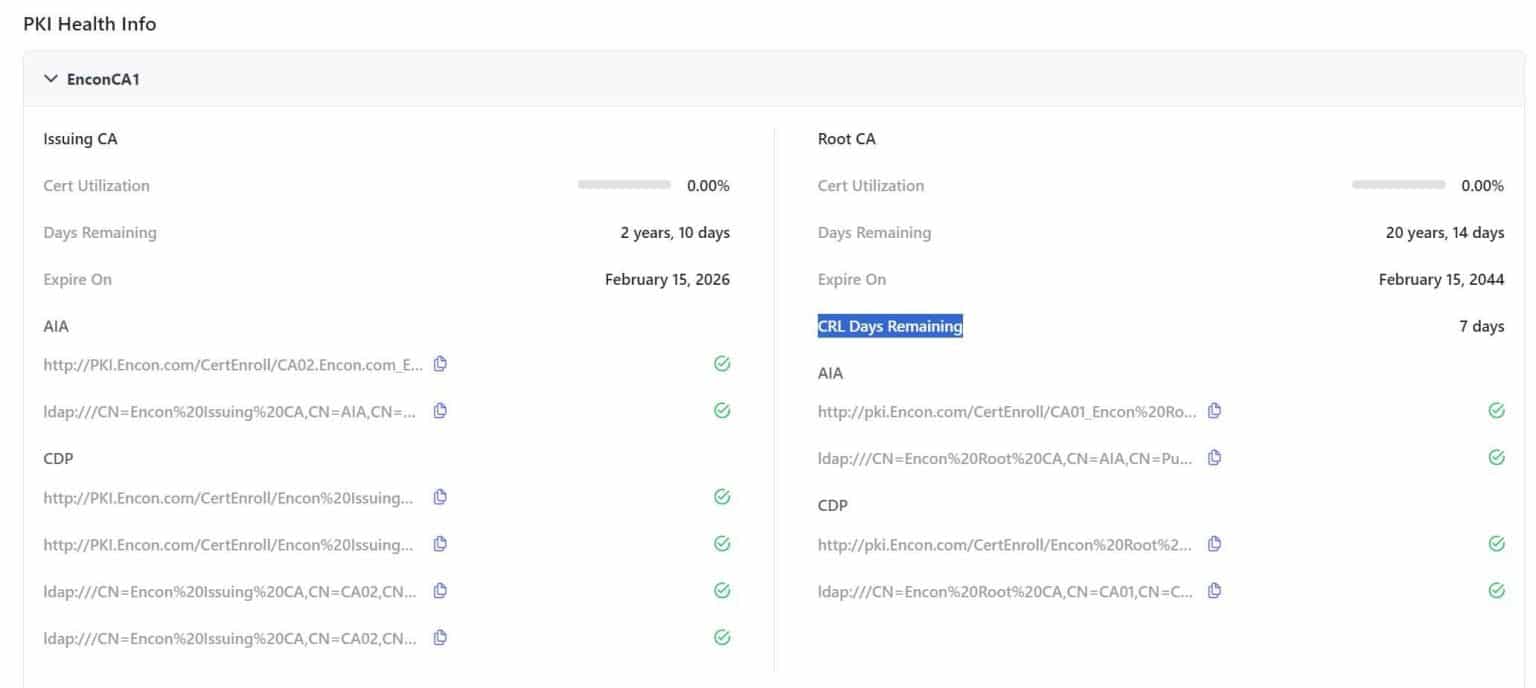
CertSecure performs a detailed check of all the Certification Authority components and showcases all the CDP and AIA, along with the remaining days for the CRL. If a failure is detected, the solution automatically alerts the admins about the issue.
- Detailed Check: CertSecure verifies all the certification authority’s components and provides a centralized view of the PKI health.
- CDP, AIA points: It identifies the CDP and Authority Information Access (AIA) points for locating the CRL.
- Remaining Lifetime of CRL: It displays the remaining lifetime before the CRL expires. This helps admins to update the list and mitigate the risk of relying on outdated CRL.
- Automated Alerts: CertSecure provides an integrated alerting mechanism to notify the admins about the expiration, as well as incident management in case of failures related to CRLs.
Conclusion
In Conclusion, a CRL maintains the digital communication secure by promptly revoking compromised / invalid certificates. It is an effective solution to ensure the trust and integrity of the overall web communication. But an expired, offline, or incorrectly configured CRL can result in service interruptions and outages.
Thus, using a CLM solution like CertSecure helps in centrally monitoring the digital certificates and CRLs across the organization. This would further help in preventing outages, decreasing downtime, and saving on potentially costly remediation.