Secure file transfer protocol is a transfer protocol in which Secure Shell encryption is used to ensure a high level of security when sending and receiving files, used to securely transmit data between a local system and a remote end server, in the form of audio, video, and files. It is based on the File Transfer Protocol (FTP) and contains Secure Shell (SSH) security components. SFTP supports a variety of authentication mechanisms to provide authentication, including user IDs and passwords, SSH keys, and combinations of the two. What makes it different from other protocols is the use of encryption and authentication methods, which are exceptionally mandatory as file transfers through the internet can consist of users’ personal and financial information.
What Is SFTP and How Does It Work?
SFTP is also known as SSH File Transfer Protocol, Secure File Transfer Protocol, and Secret File Transfer Protocol. It works on the Network Layer Protocol and ensures a secure data exchange between the client-server architecture over a stable network connection. It was designed by the Internet Engineering Task Force (IETF).
Some of the Information a System Needs to Configure for an SFTP Client:
-
Server Hostname
Provide the server’s hostname or IP address.
-
Port Name
The client’s TCP port of choice when connecting
Ex: Port no – 22 or other
-
Security Protocol
Choose the protocol you wish to use to create a secure connection.
Ex: SFTP, FTP, SCP, or other
-
Username
Username by which the client wants to connect to the server
Ex: Username: Admin
-
Password
The password assigned to the user.
Ex: ******
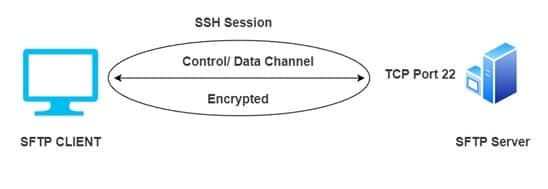
To avoid password sniffing and revealing critical information in plain text, SFTP transfers files securely via SSH and encrypted FTP instructions. SFTP also safeguards against man-in-the-middle attacks since the server must authorize the client.
Uses of SFTP
SFTP can be used anywhere file security is needed. One of the primary uses is Compliance with requirements such as the federal Health Insurance Portability and Accessibility Act (HIPAA), which oversees protected health information. Even any third-party worker associated with the Hospital or Healthcare must keep their information confidential, and that’s when SFTP is very useful. SFTP is one of the numerous solutions for securing the data during transfer, ensuring that hackers do not gain access to it and that the organization does not inadvertently violate HIPAA if that law applies. Other data security standards like CCPA or GDPR can also be met using SFTP.
SFTP Encryption
Encryption has a significant role in SFTP. It protects data from hackers or any unauthorized person by converting it into an unreadable format so that no one can access it or tamper with it during the transmission process. After it reaches its destination, it is again converted into a readable format by authorized users using the key provided to the user. The SSH Encryption method is used during the file transfer to secure the process. It can be done in various ways:
- One of the ways is to encrypt the network before commencing the file transfer and generate the password to log on to the network using the automatically generated pairs of private and public keys.
- Another way is to utilize the manually generated private and public keys to perform the authentication procedure, allowing the user to log in to the network without a password.
Applications of SFTP:
- Mainly used to share sensitive data between two sources securely, it is used to undertake audits and transmit data and reports between the company and regulatory organizations.
- SFTP provides us with functionalities to create, import, export, and delete files and directories. This helps in quick access to data from anywhere.
- By the use of an updated authentication process, secret file-sharing can also take place.
Advantages of SFTP
There are various advantages of SFTP as a service
- Data Security: When dealing with sensitive and personal data, data security is a big question nowadays. You want your files to be fully secured. SFTP provides various ways of Secure Data Transfer. SSH File Transfer requires the use of keys, usernames, and passwords so that no intruder can get access to it.
- No Hardware Needed: Using SFTP doesn’t require any extra utilities like servers or infrastructure; once you enter into SFTP services, all facilities are immediately available for use.
- Accessibility: From an Accessibility point of view, SFTP provides a single location to store all of its business files and gives you complete control and flexibility over it.
- Speed and Efficiency
- Reduce Costs
Conclusion
We have discussed what SFTP is; SFTP is a transfer protocol in which SSL encryption ensures a high level of security when sending and receiving files. Then we listed the information a system needs to configure an SFTP client. Uses of SFTP include Compliance with requirements such as the federal HIPAA, which oversees protected health information. The SSH Encryption method is used during file transfer to secure the process, and it can be done in various ways. Then, we discussed the Applications and Advantages of SFTP, making our discussion complete.




