How to secure IoT vulnerabilities?


Internet of Things (IoT) security is the technology segment that is focused on safeguarding connected devices and networks in IoT. It involves adding internet connectivity to a system of interrelated computing, mechanical and digital machines, or devices. A few examples of IoT are:
The various concepts are as follows:
Focus on real-world data
An enterprise has to deal with various types of documents and data in different forms of static digital information. IoT devices produce the type of data that typically reflects more than one physical condition in the real world and helps exercise control over what is happening in real-time.
Resulting Data itself
IoT tasks are often defined by a larger purpose that drives their deployment. In many case scenarios, data is part of a control loop with a straightforward cause-and-effect objective. For example, a house owner can know if any of their doors are unlocked or not through the sensor, and through that transmitted signal, use an actuator to lock that door immediately.
IoT works as a group of devices, networks, and software tools combined to form an ecosystem to collect, send and act on data that they acquire from their environments. IoT consists of devices that “talk” to the cloud through connectivity. When this data gets to the cloud, the software processes it and then performs an action on it (upon a decision made). But the most important thing about an IoT system is – this whole process is customizable.
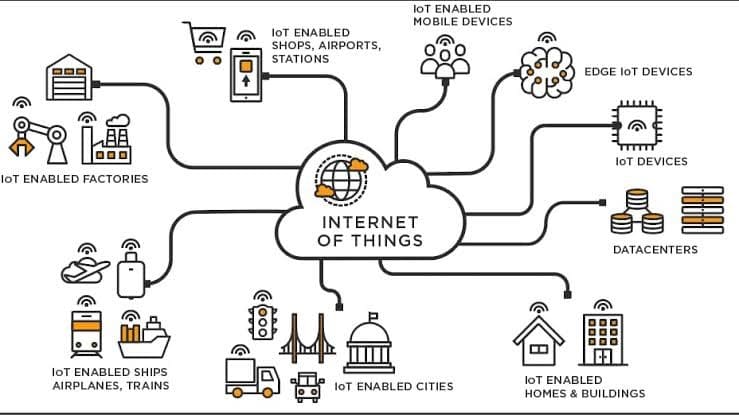
IoT devices don’t have any built-in security measures, making them vulnerable to attackers. Most of these IoT devices are interconnected, so if one is compromised, multiple devices will be too. A few of the security measures are:
Change default router settings
To preserve the security of private Wi-Fi, a user needs to rename the router and not stick to the name given by the manufacturer. Network and Wi-Fi are the first defense against attackers because multiple IoT devices are connected to the Wi-Fi. A user should change the default privacy and security settings and avoid online shopping using public Wi-Fi, to prevent attackers from stealing data.
Pick a strong password and not overuse it
Using a common and simple password is like an open invitation for hackers or attackers; strong and secure passwords are the best defense against attackers. A user needs to use a new and unique password for every possible IoT device because if an attacker guesses one of the user’s passwords, the attacker could harm every device with that same password. This may sound troublesome to remember all the passwords, but it is essential to secure IoT devices.
Keep software and firmware updated
Firmware keeps a user protected by using the latest security patches and reduces the chances of cyber-attacks. This can also fix most of the vulnerabilities or exploits which emerge as well as secure IoT devices.
Avoid using Universal Plug and Play
Universal Plug and Play (UPnP) has its uses but it can also make various IoT devices like routers, cameras, and printers vulnerable. The main principle behind designing UPnP is to make it easier for network devices to connect without any additional settings or configurations. However, this benefits hackers more than users, as hackers can discover all IoT devices in that local network. So, it’s better to turn off UPnP completely.
Protection against Physical Tampering
Hackers can tamper with the device and get control of it. With millions of devices being installed nowadays, it is relatively easier to reach and get hold of, by an attacker. Physical tampering can be done in various ways like – connecting to exposed ports, device theft, interrupting the device’s power, removing parts, and so on. The user needs to ensure that the product or IoT device doesn’t have any exposed parts or connectors and should implement locks so that only an authorized person has access to the device.
Pick a strong password and not overuse it
Using a common and simple password is like an open invitation for hackers or attackers; strong and secure passwords are the best defense against attackers. A user needs to use a new and unique password for every possible IoT device because if an attacker guesses one of the user’s passwords, the attacker could harm every device with that same password. This may sound troublesome to remember all the passwords, but it is essential to secure IoT devices.
Securing communication channels
All the devices in an IoT system must communicate with each other and with other cloud apps or services. It is important to ensure these communications are secure, like encrypting all the messages before sending them over the network and using robust TLS protocols.
To ensure a secure and reliable IoT environment, several key security requirements must be addressed:
Validation and Sanitization
Ensuring the accuracy and cleanliness of data received by devices helps prevent manipulation and malicious attacks.
Hash Functions
These functions act like digital fingerprints, verifying that data hasn’t been tampered with during transmission.
Message Authentication Codes (MACs)
Similar to signatures, MACs confirm the origin and integrity of messages exchanged between devices.
Unique Identifiers
Assigning unique identifiers to each device allows for clear identification and prevents unauthorized access.
Hardware-Based Identity
Utilizing tamper-proof hardware components further strengthens device identity security.
Identity Management
Implementing processes to manage the lifecycle of device identities, including creation, updates, and deactivation, ensures proper control.
Customizable Security Policies
Adapting security measures to meet industry-specific regulations is crucial for compliance.
Audit Trails
Maintaining detailed records of device activities allows for auditing and helps demonstrate adherence to regulations.
Secure Logging
Ensuring log entries are tamper-proof and readily accessible facilitates security investigations and compliance audits.
Mutual Authentication
This two-way verification process confirms the identity of both communicating parties, preventing impersonation attempts.
Secure Channels
Encrypting data transmission through dedicated tunnels or virtual private networks (VPNs) protects against eavesdropping.
Transport Layer Security (TLS)
Utilizing the latest TLS protocols and ciphers strengthens the encryption used for secure communication.
Real-time Monitoring
Keeping a watchful eye on device activities and communication allows for prompt detection and response to security threats.
Automated Reporting
Generating automated reports provides valuable insights into the overall security posture of your IoT ecosystem.
Cybersecurity has many considerations, ranging from encryption to identity management, authentication, authorization, etc. Security is not a one-time thing, hackers or attackers are always looking for new ways to exploit vulnerabilities and cause harm, so security needs to become a standard part of building and managing products.

February 14, 2025

January 24, 2025