GitLab is a web-based Git repository manager that provides source code management, continuous integration/continuous development (CI/CD) pipeline automation, and several other features for software development. It is a comprehensive DevOps platform that enables experts to carry out every project work, from planning and managing the source code to monitoring and security.
Teams can collaborate and create better software as a result. GitLab offers comprehensive DevOps capabilities throughout every stage of the software development lifecycle. Its continuous integration (CI) capabilities automate the building and testing of code for development teams. The platform also includes security features that provide scan results within the native CI pipeline/workflow, and a dashboard that assists security professionals with managing vulnerabilities.
Codesigning
Code signing is a procedure that verifies the legitimacy of the author and the originality and authenticity of digital information, particularly software code. It also ensures that the information is not malicious code. Additionally, it guarantees that this information has not been altered, falsified, or canceled after being digitally signed. The digital signature is created using a private key that’s only available to the software’s publisher. When the software is downloaded and installed, the digital signature is checked against the public key to confirm that it matches and that the software hasn’t been modified. Code signing is important for ensuring the safety and security of software applications, as it helps prevent the distribution of malware and other malicious software.
Encryption Consulting has a CodeSigning solution, “CodeSign Secure,” which can help you with tamper-proof storage for the keys and complete visibility and control of Code Signing activities. The private keys of the code-signing certificate can be stored in an HSM to eliminate the risks associated with stolen, corrupted, or misused keys.
Integration of GitLab with CodeSigning
To get started with this, you’ll first require a GitLab Account and a Runner, where you’ve signtool and ECSigning KSP installed and configured. Listing down the pre-requisites:
- Self Hosted Runner which has ECSigning KSP, Signtool installed and configured. This runner should be provided with Administrative privileges.
- A GitLab Account.
To set up the ECSigningKSP and Signtool, go through the following steps:
Download Windows SDK: (developer.microsoft.com/en-us/windows/downloads/windows-10-sdk/)
You can choose to install only the Windows SDK Signing Tools for Desktop Apps.
Open the winsdksetup.exe file. Remember the default path shown in the install path, as this will be helpful with running these commands from the command prompt.
On the Windows Kits Privacy page, either option for allowing Microsoft to collect insights is okay. Click next.
Accept the license agreement

Deselect every feature except for Windows SDK Signing Tools for Desktop Apps, then select install.
When prompted if you want to allow this app to make changes, select yes.
Click on windows search bar on task bar and type “Edit the system environment variables” and select the control panel option of the same name.
Click environment variables.
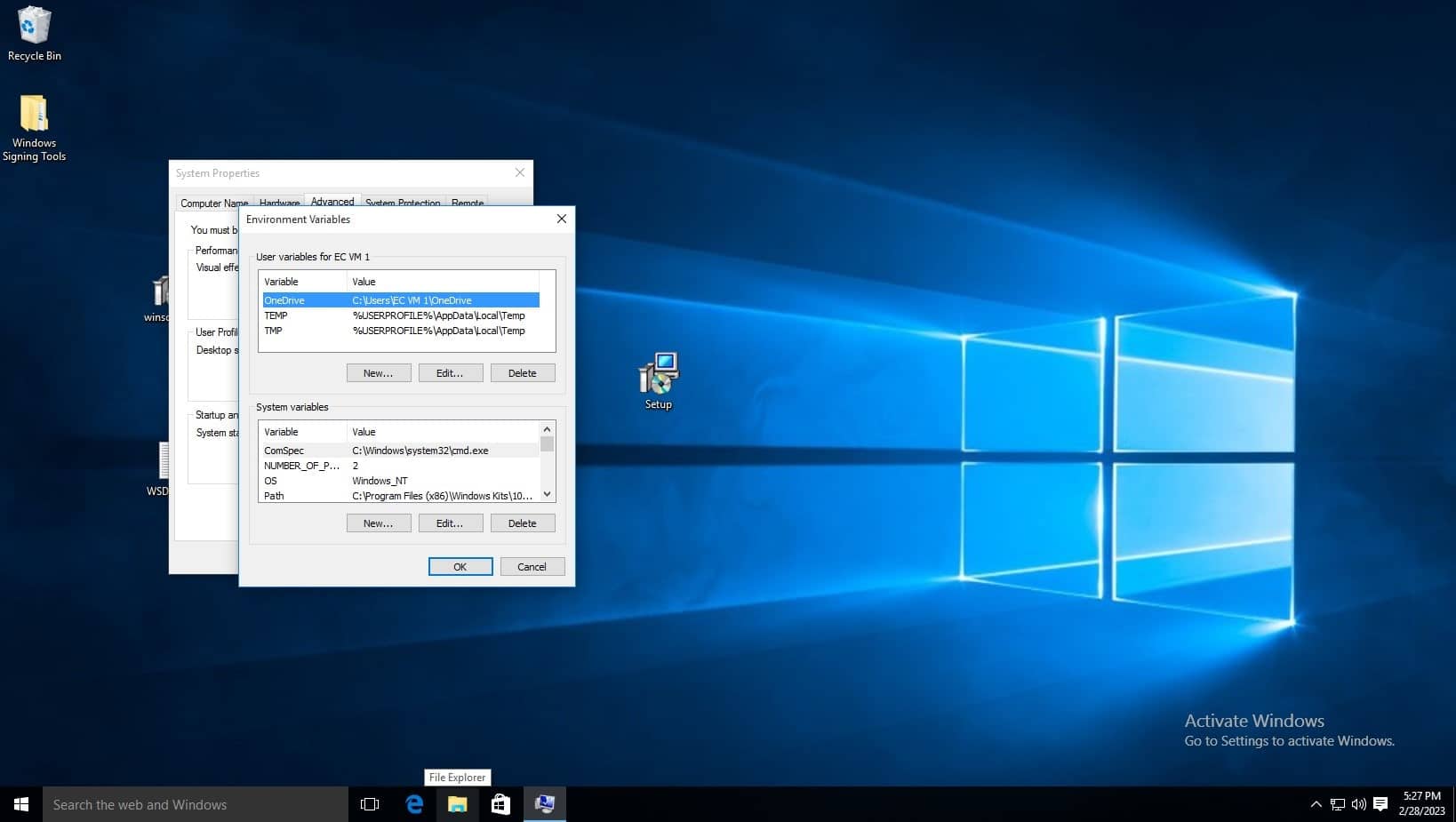
Before editing the variable list, navigate to where the Windows SDK is installed to using file explorer, you must copy the path of the folder which contains the signtool application, the default path is C:\Program Files (x86)\Windows Kits\10\bin\10.0.22621.0\x64, refer to the below screenshot. Make sure to right click and copy the path as shown. You can also see the signtool application at the bottom of the file list, this is the command you will run.
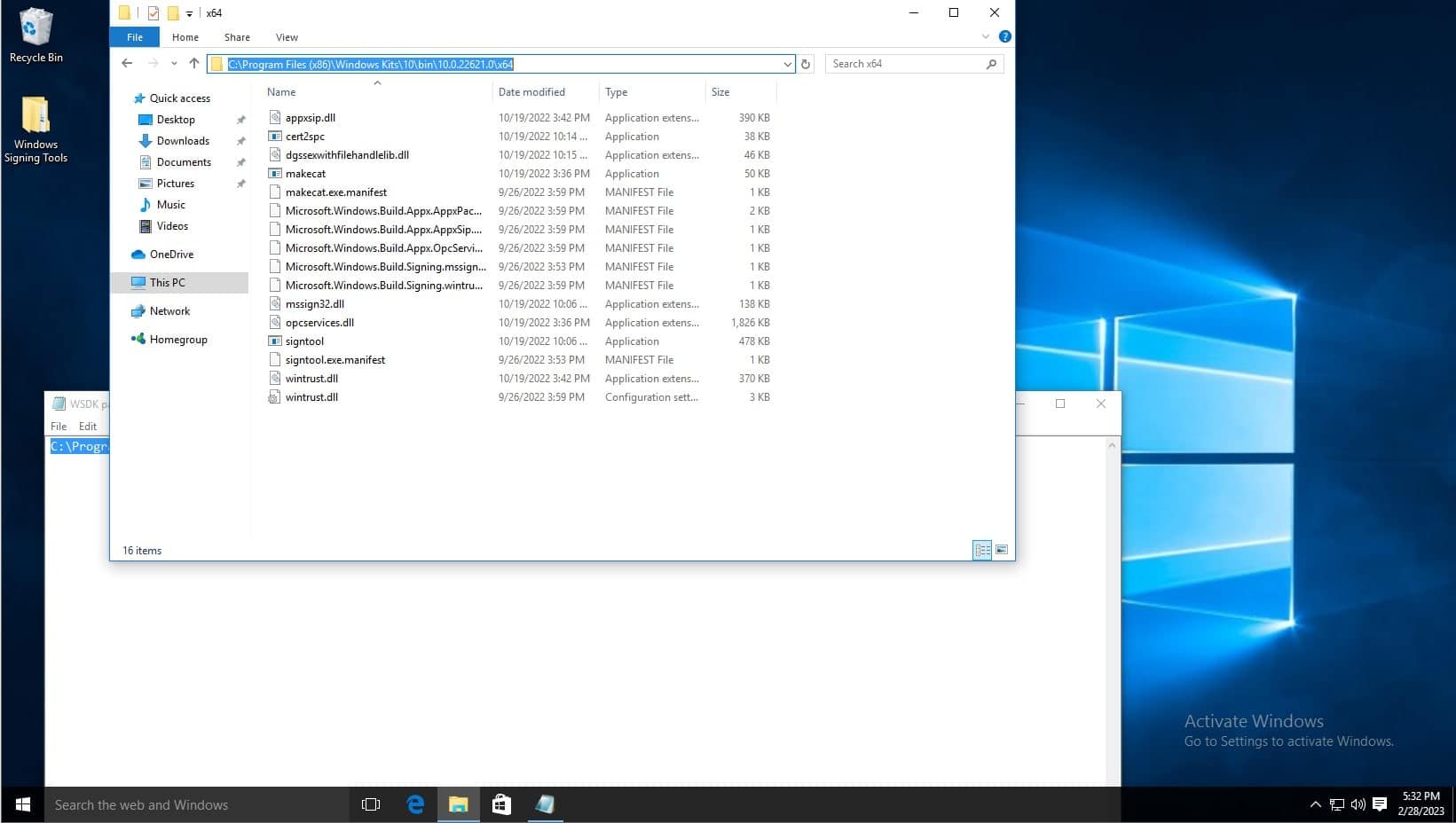
In the System Variables list, click new. Then type Path as the variable name, and copy and paste the aforementioned path. Then click OK on the environment variables window and system properties window.
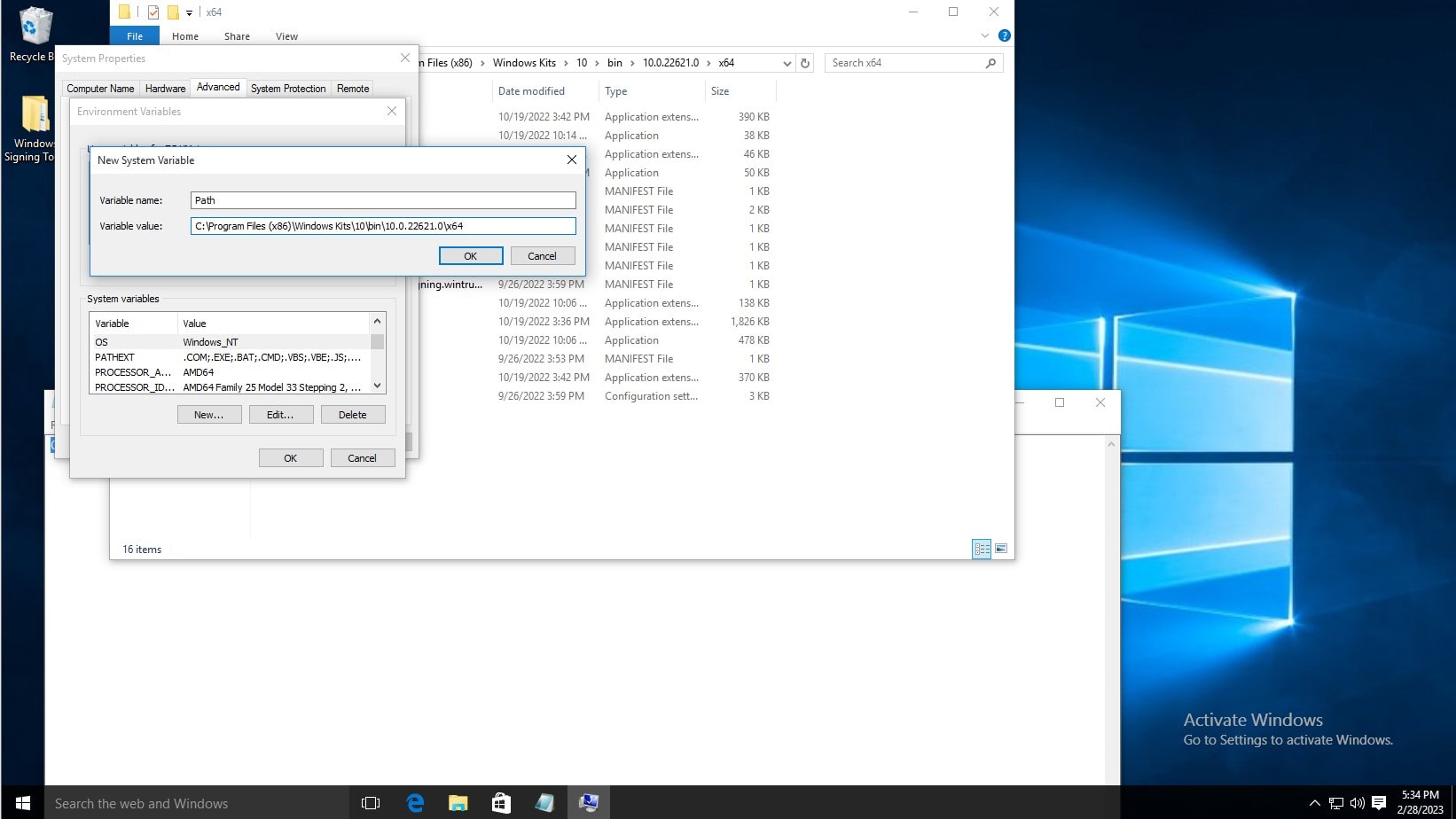
To test the installation, open command prompt, and type signtool, and the output should be as shown below.
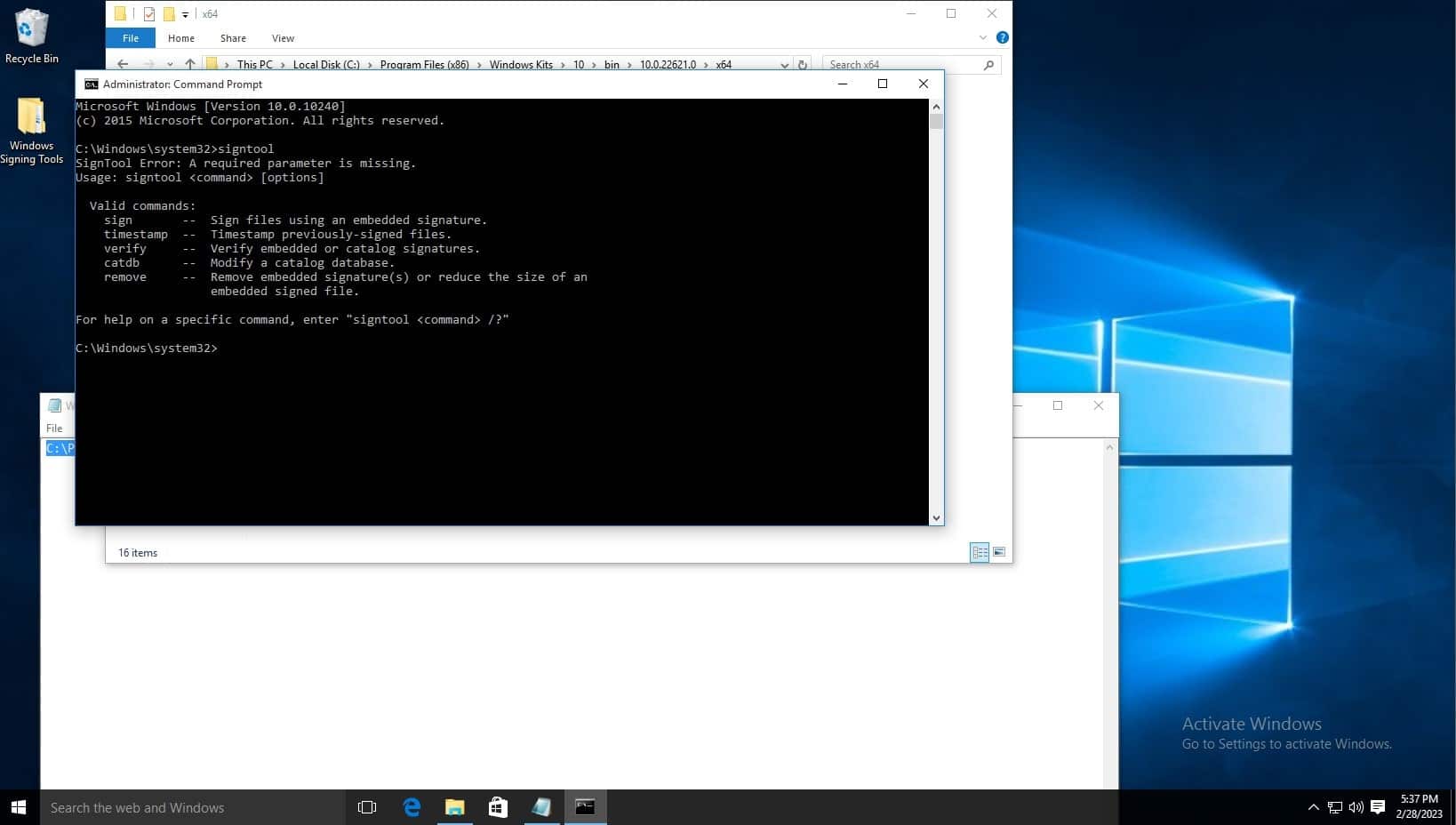
The default signtool installation location is, for example: C:\Program Files (x86)\Windows Kits\10\bin\10.0.22621.0\x64
To set up KSP follow the steps below:
If you’re using our solution you can download the KSP using the steps below:
- Sign in to Code Sign Secure.
-
Navigate to: Signing tools repository.
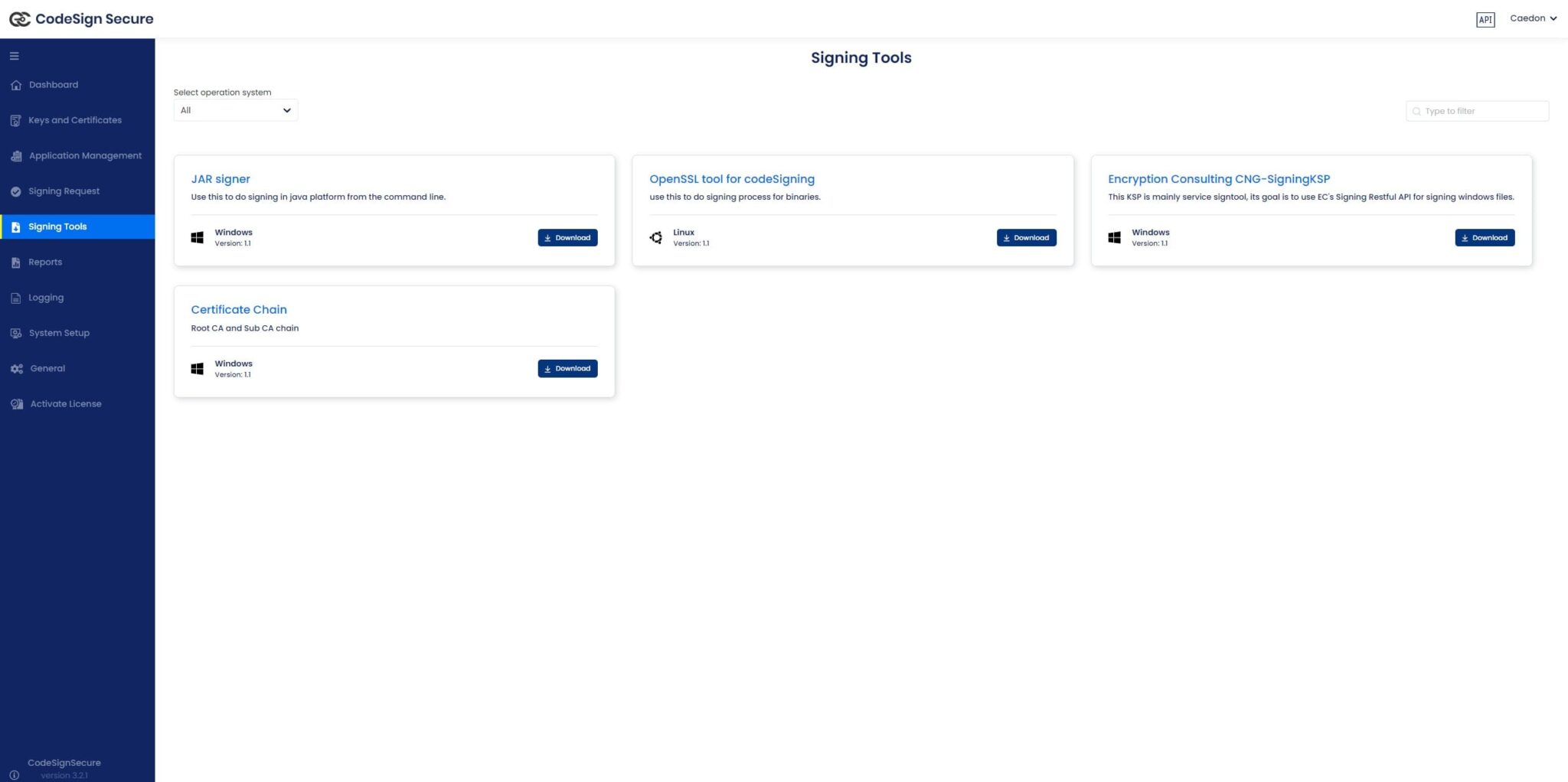
- Download “Encryption Consulting CNG-SigningKSP”
-
Install the client tools using the .MSI installer. The .MSI installer automates much of the configuration. Navigate to where the downloaded file is saved and launch the installer.
-
Click next when the installation wizard appears.
-
Click next.
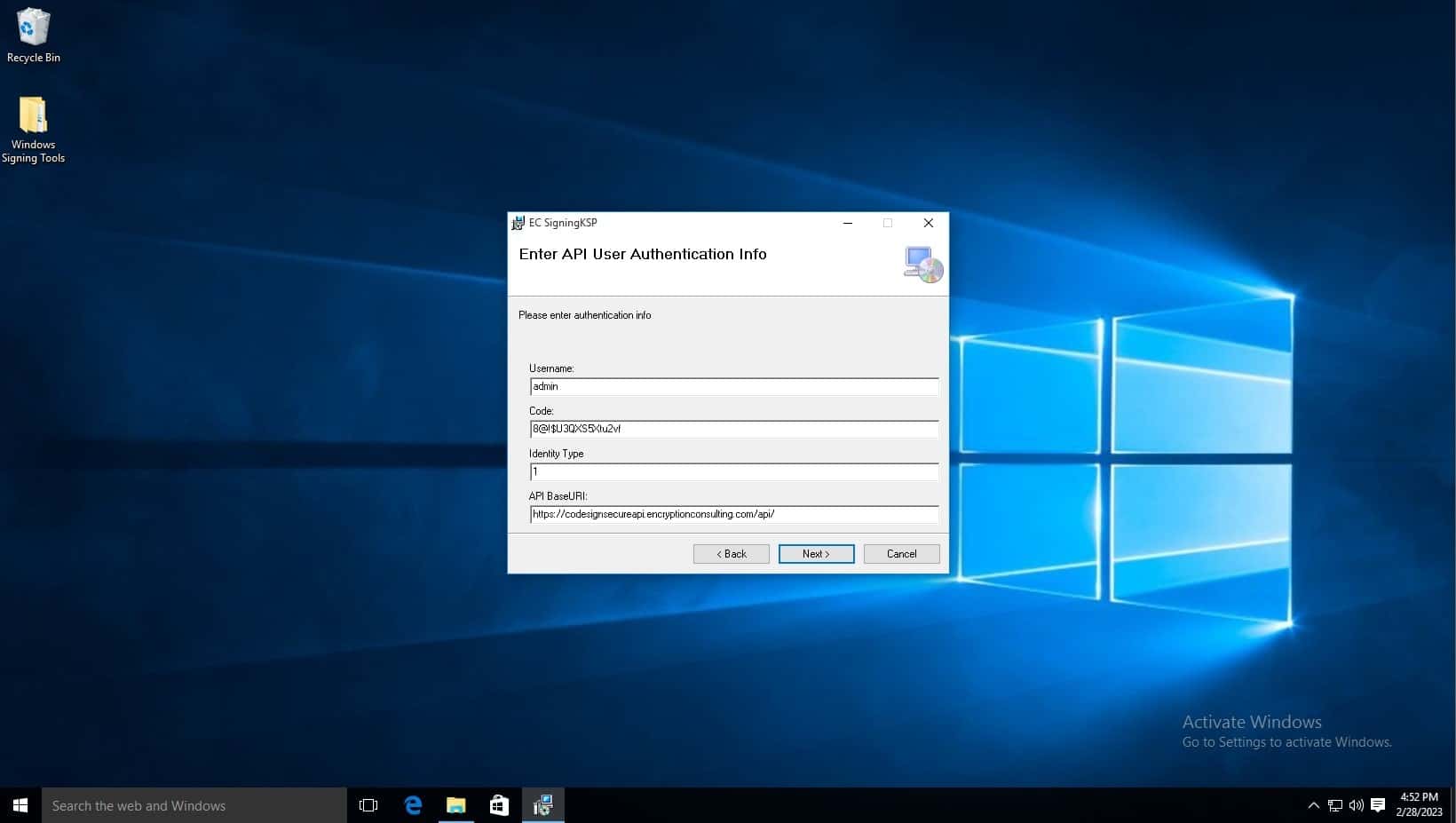
- In the Username field, type admin.
-
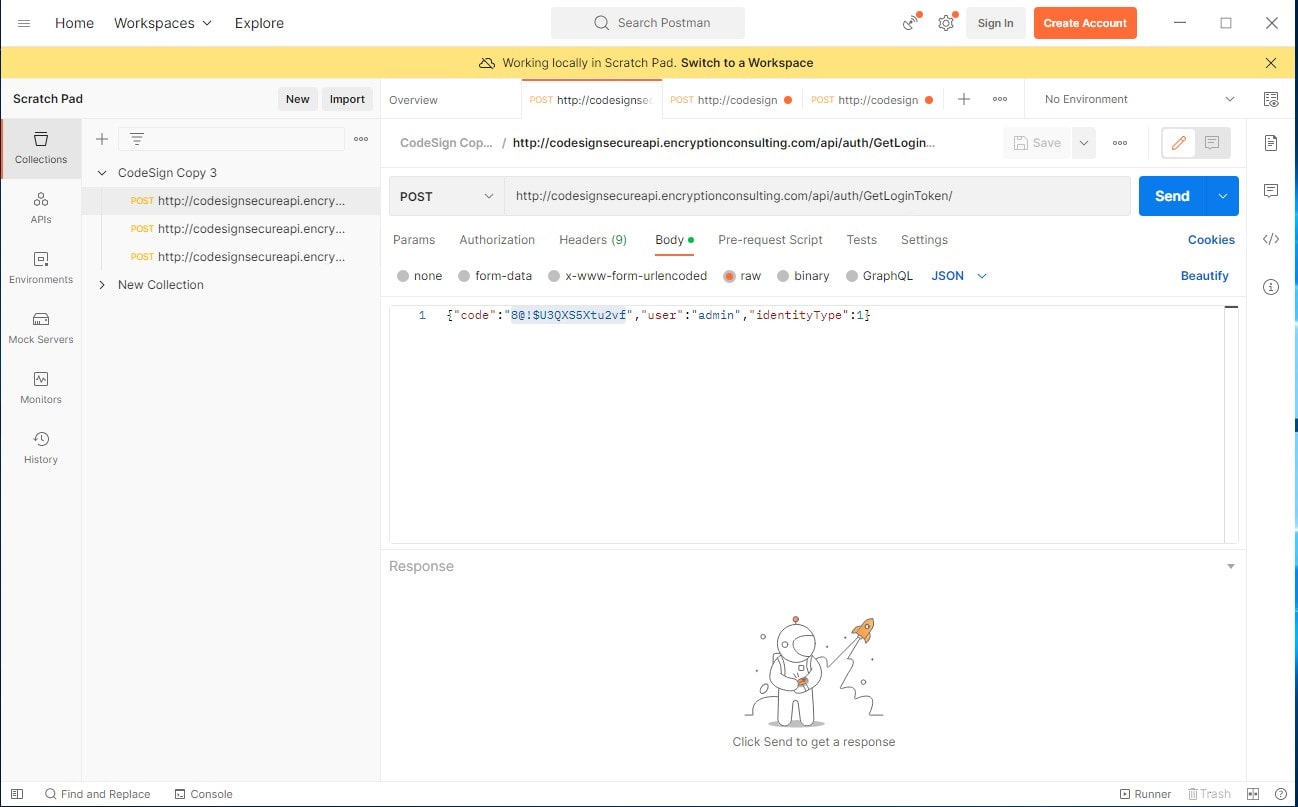
In the Code field, copy the code from the Postman API Repository. Click on the GetLoginToken api and copy the code from the Body.
Download PostMan from this link. Once downloaded, click the skip button at the bottom of the window. Once on dashboard, add a new collection using the plus sign button next to collections.
GetLoginToken API (http://codesignsecureapi.encryptionconsulting.com/api/auth/GetLoginToken): This is the most important API, as this gives you a Bearer Token to use with the rest of the APIs, What should be in the body is shown below. The code serves as a password in order to get a the Bearer Token, the user field is the username, and the identity type field specifices the user type. Click Send to generate an output which has the Bearer Token listed at the bottom. Copy this token for use.
- Change the Identity Type to 1.
- Leave API BaseURL the same.
-
Click next.
-
Click next.
-
You will then be notified that this program will make changes to your pc, click yes.
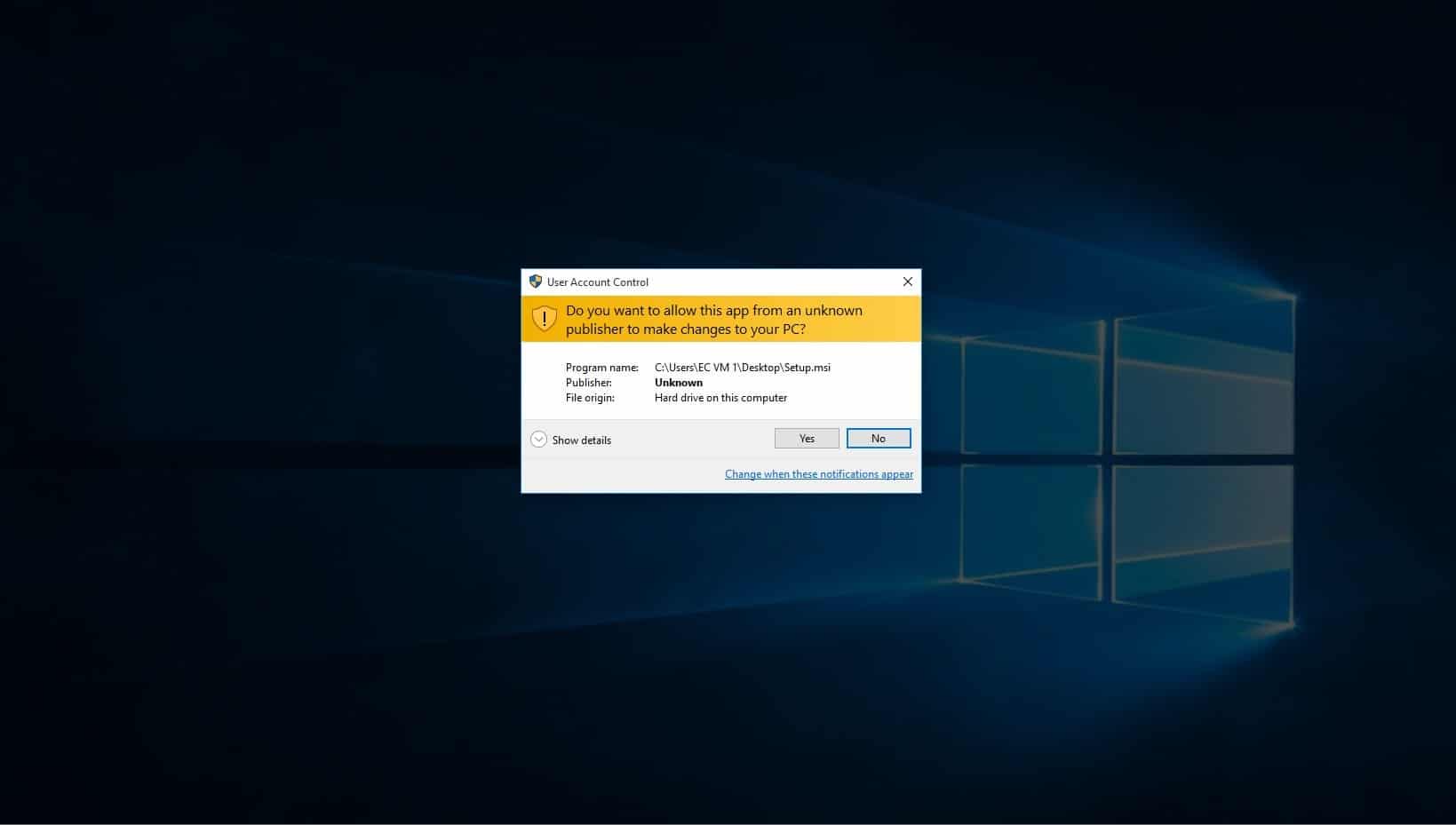
-
Installation is now complete.
Please follow the steps below:
- Set Up a GitLab Account. Navigate to creating a New Blank Project.
-
Scroll down to settings -> CI/CD and navigate to runner. Expand it.
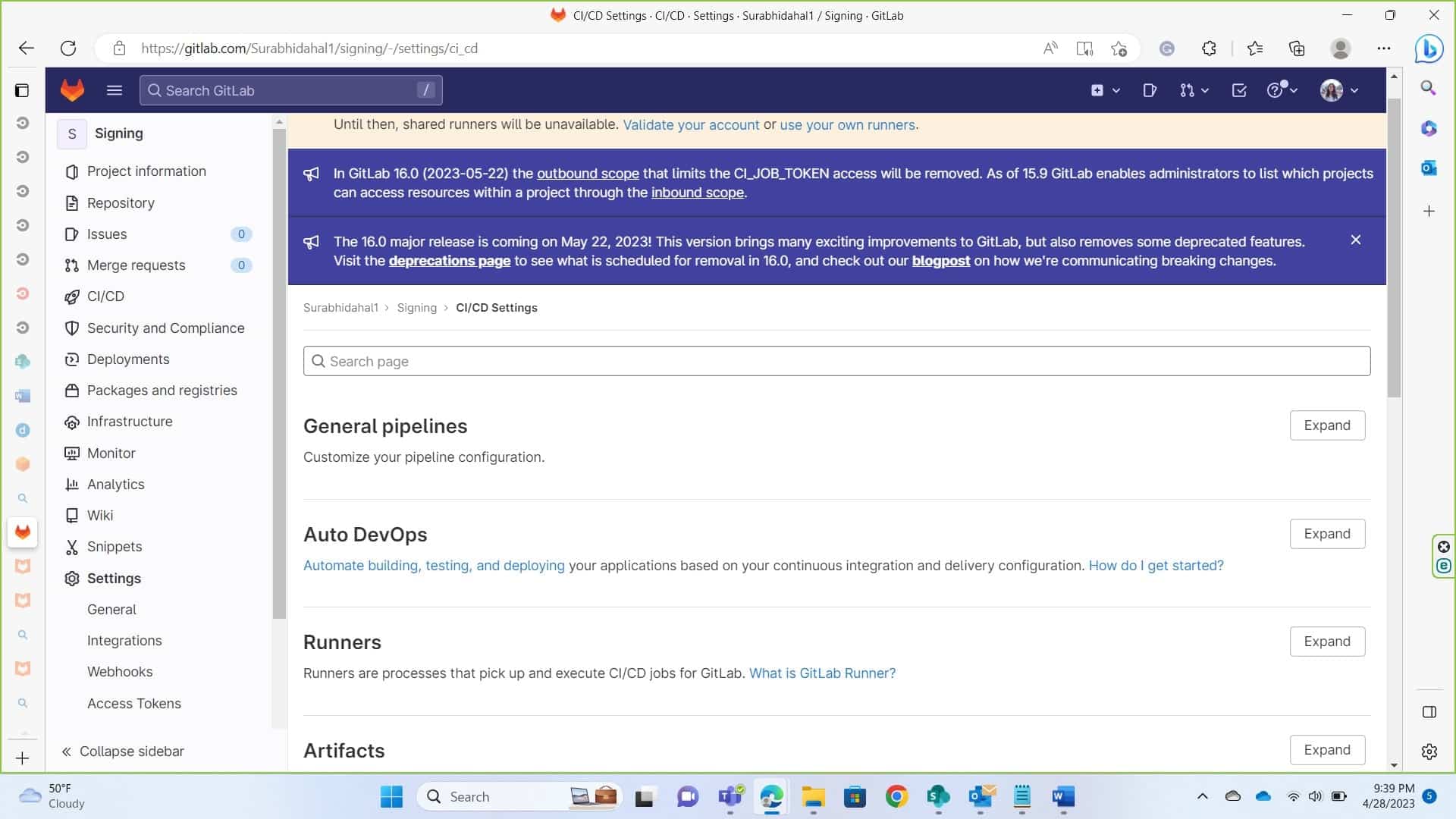
-
Click on new project runner.
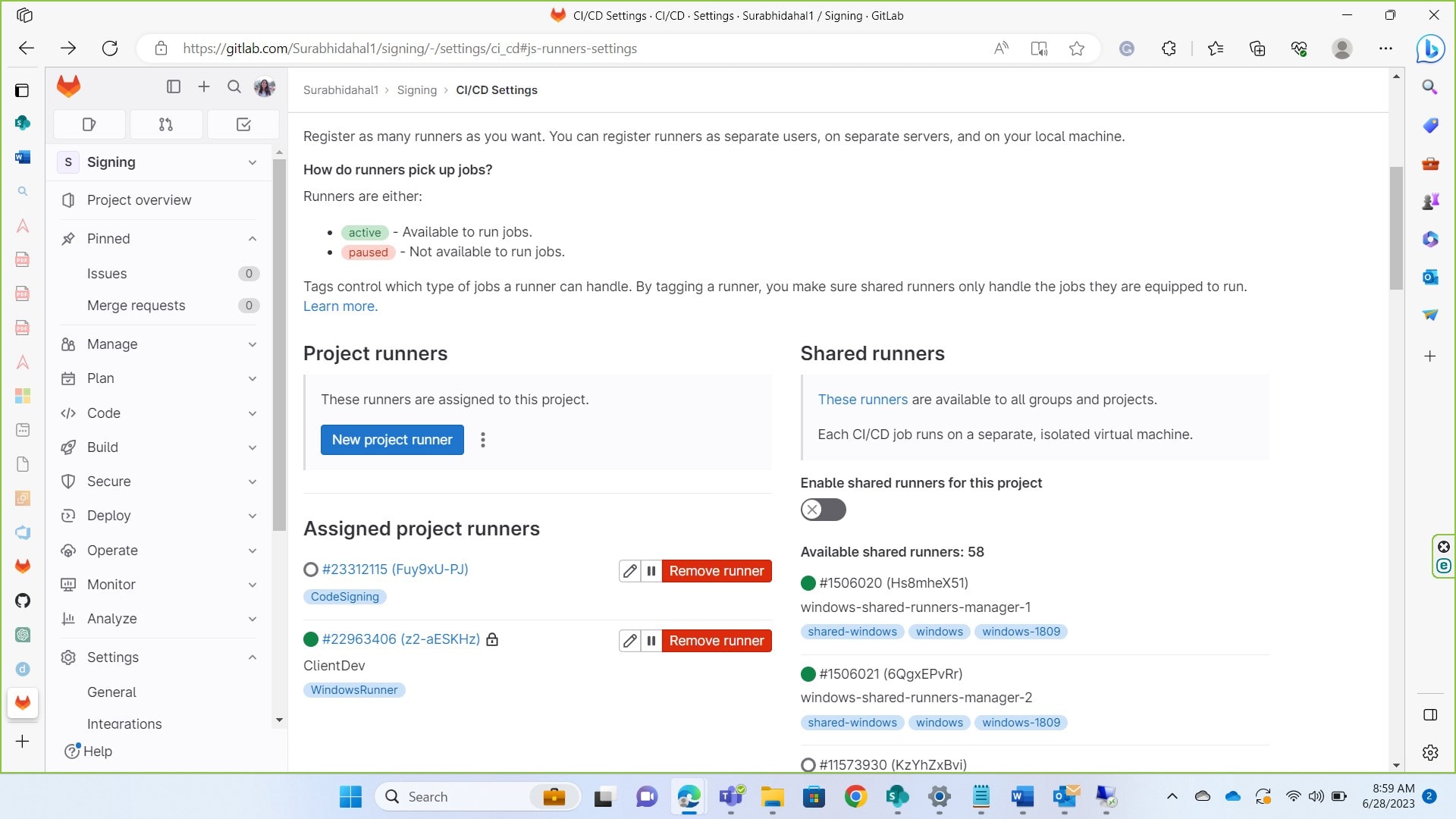
-
Click on platform of your choice and provide a tag for the runner. Give timeout seconds and click on create runner.
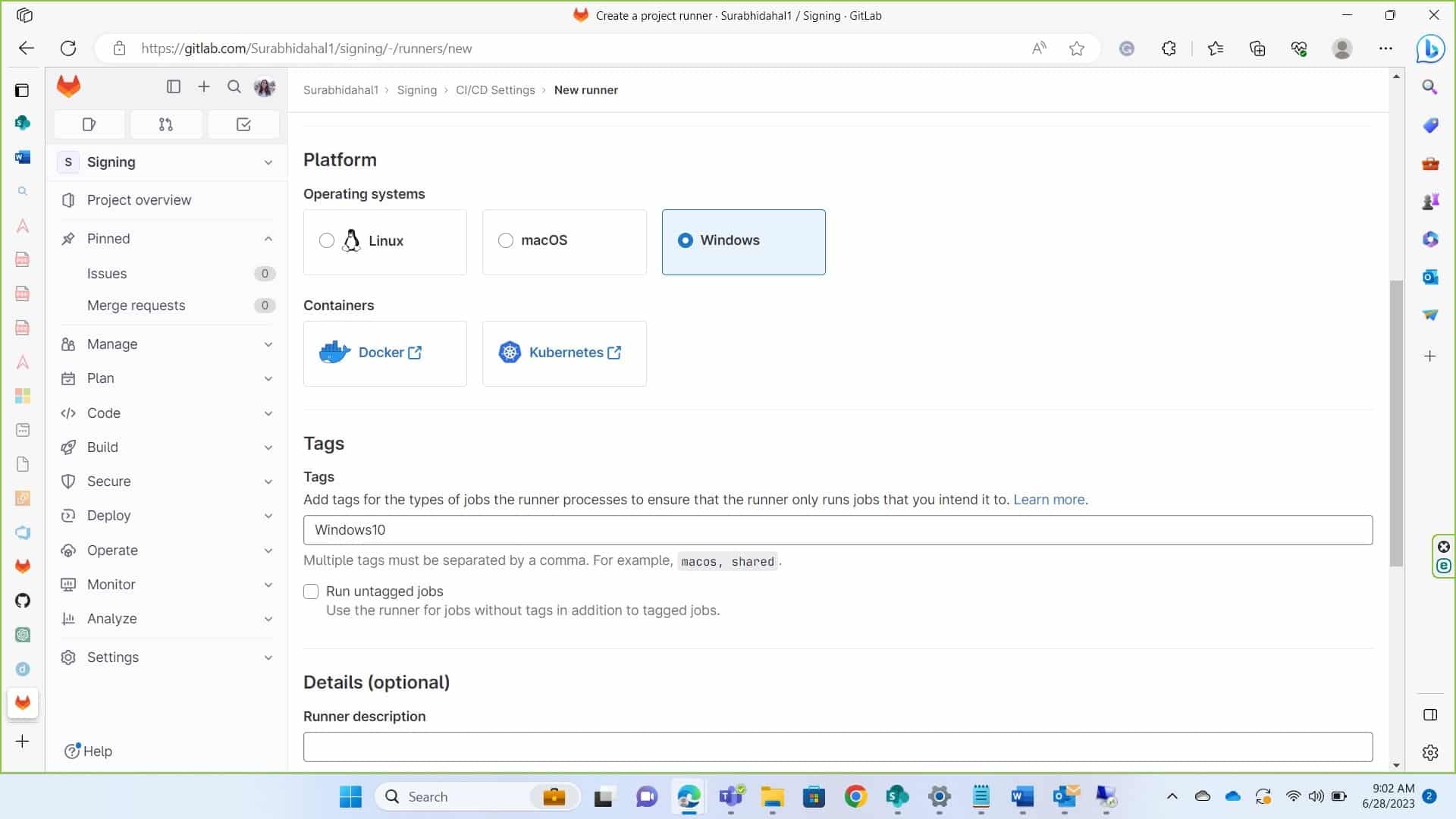
- Copy the token displayed we’ll need it to register the runner. Now we’ll first install Gitlab runner in our device.
- Install GitLab runner in your device using the link. This link is for Windows. You can look this link to see steps to Install it in your specific device.
- You can follow the documentation to set up your runner and register it as per your device.
To register a runner under Windows, run the following command:
- .\gitlab-runner.exe register
- Enter your GitLab instance URL (also known as the gitlab-ci coordinator URL). Example: https://gitlab.com
- Enter the token you obtained to register the runner. You can access this from settings -> CI/CD -> Expand -> Project runners. Under project runners you can find token.
- Enter a description for the runner. You can change this value later in the GitLab user interface. Example: Device
- Enter the tags associated with the runner, separated by commas. You can change this value later in the GitLab user interface. Example: WindowsRunner
- Enter any optional maintenance note for the runner.
- Provide the runner executor. We’re operating this in Shell.
Once the runner is installed and configured, navigate to services in your device, scroll down to GitLab Runner and set log on as Administrator. Provide Admin Password here.
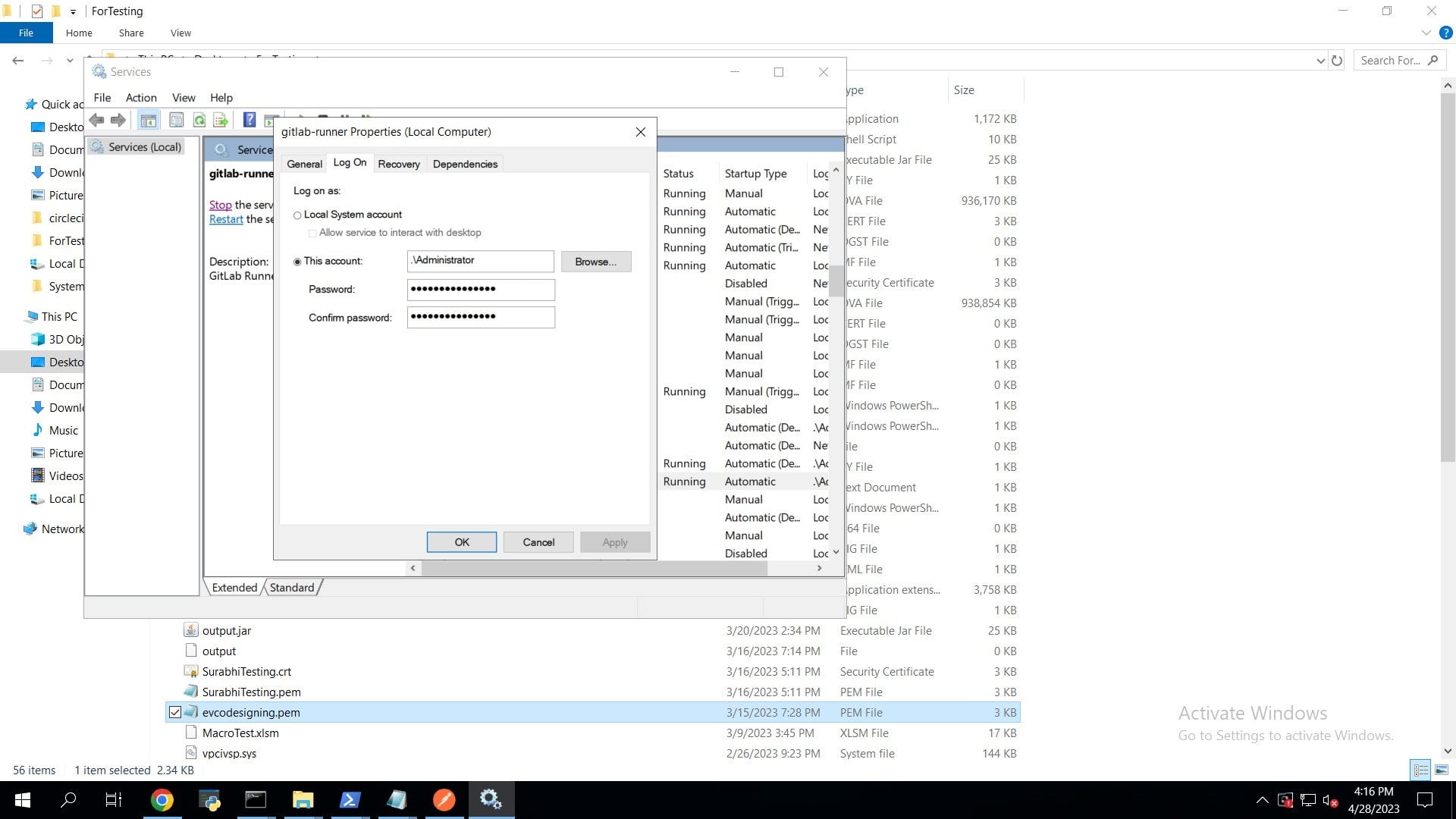
Once this is done, go to your project. You might have to rename the .ym file name. Rename it as .gitlab-ci.yml. Run the script below to perform codesigning.
job1:
tags:
- WindowsRunner //The tag you provided while setting up the runner
script:
- signtool sign /csp "Encryption Consulting Key Storage provider" /kc evcodesigning /fd SHA256 /f "C:\Users\Administrator\Desktop\ForTesting\evcodesigning.pem" /tr http://timestamp.digicert.com /td SHA256 "C:\Users\Administrator\Desktop\ForTesting\AgentService.exe"
If you click on CI/CD -> jobs you’ll see it being successfully signed.
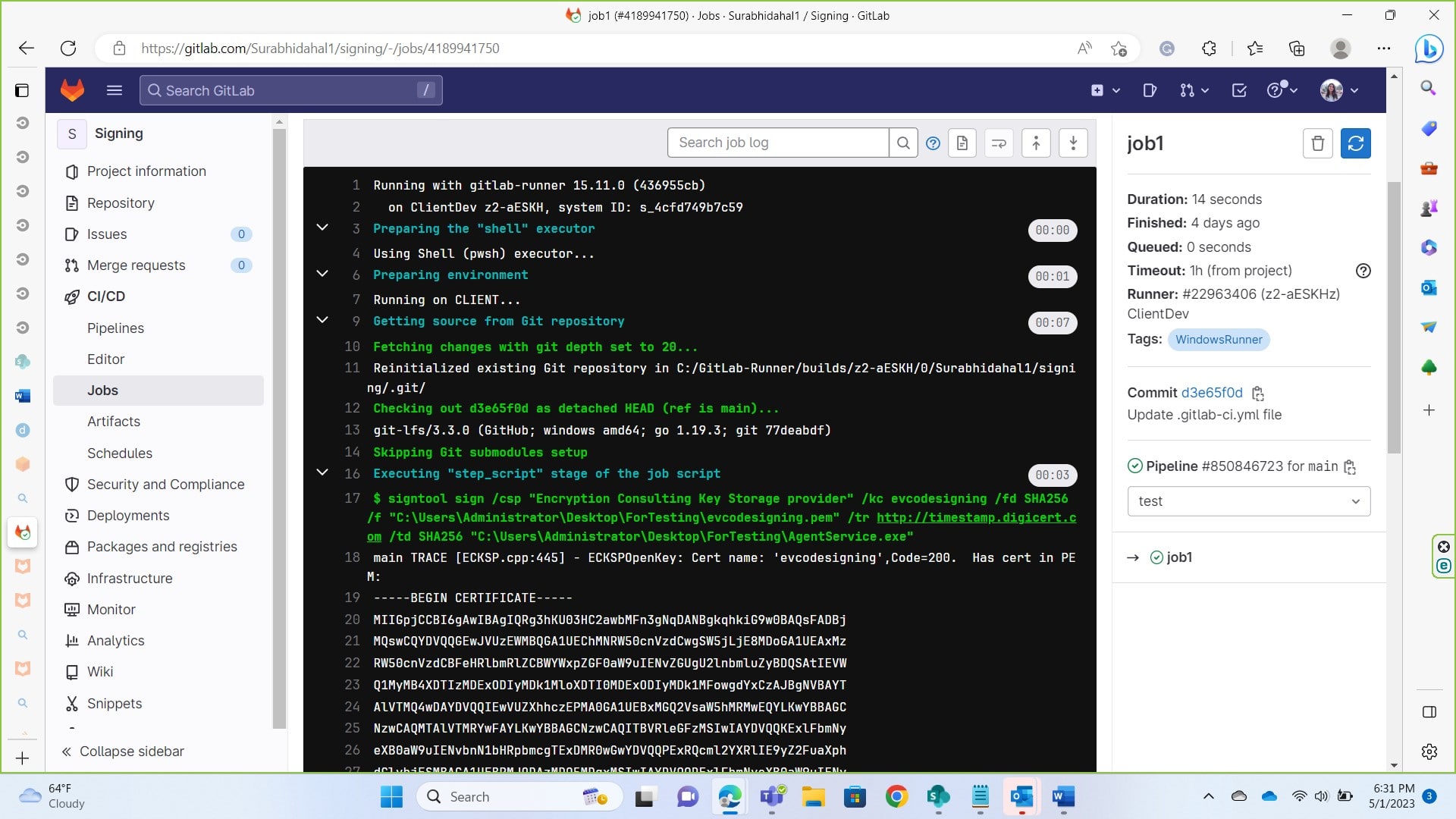
You’ll need to modify the command as per your variables
- kc evcodesigning: replace evcodesiging with your key name
- f “C:\Users\Administrator\Desktop\ForTesting\evcodesigning.pem”: replace location with location of your .pem file to perform codesiging. You can get this by using signing KSP. From command prompt reach to the directory having SigningKSP. Use command ECGetCert.ece <key name> to get pem file of your certificate.
- tr http://timestamp.digicert.com: time stamping server
- td SHA256 “C:\Users\Administrator\Desktop\ForTesting\AgentService.exe”: location of file you want to get signed.
Conclusion
The article above demonstrates the process of integration your GitLab CI/CD pipeline with codesigning. It is a very simple process as you’re just required to set up a runner, connect it with a GitLab account and build the pipeline to run the job. Codesigning is crucial in today’s date as malicious software, files continue to grow. You can contact us at info@encryptionconsulting.com for any help regarding our code signing solution.




