Setting up an Audit is one of the key aspects of any security architecture. For ADCS, logging is important as well. You may enable and set up Active Directory Certificate Services auditing using the instructions given in this article.
First Things First!
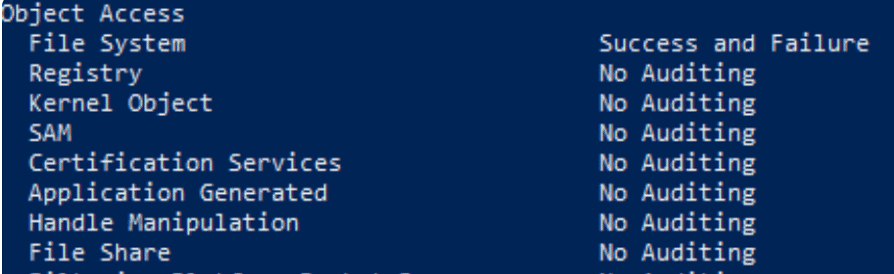
The first step is to ensure that auditing is enabled on your ADCS servers.
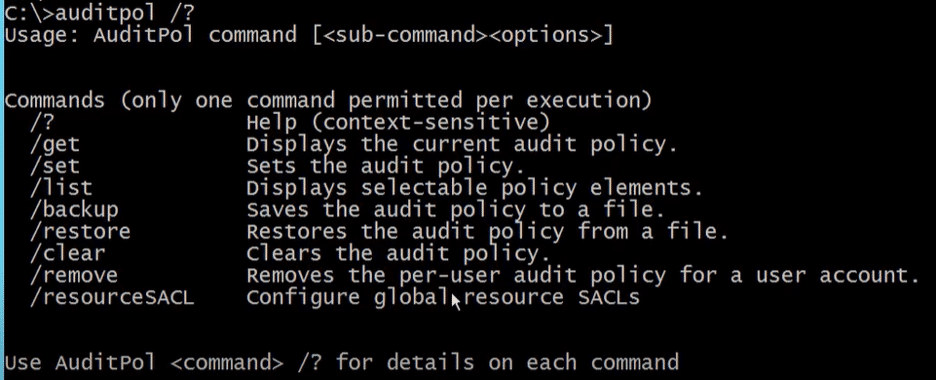
For this, run the auditpol command and make sure “Registry” and “Certificate Services” advanced auditing are turned on.
Wait, But What is Auditpol?
Windows captures logs of all kinds, which may not be useful to us and cause a lot of confusion and loss of focus. To address this, Microsoft has introduced auditpol. Auditpol is used to categorize these logs granularly at the user level.
Remember to refresh the group policy after you have enabled it!
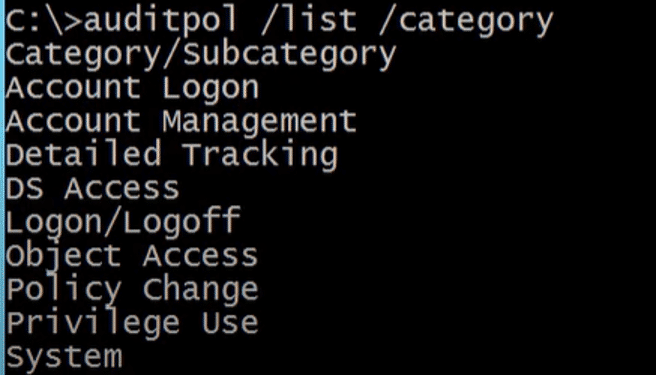
Some more examples to use auditpol are shown below :
Example 1
Example 2
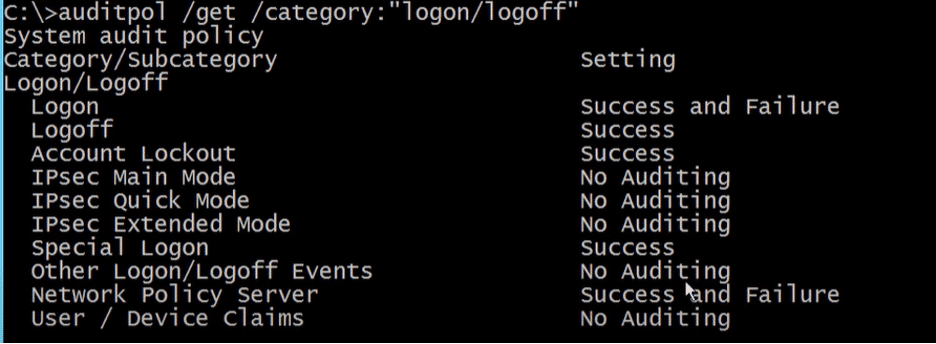
In our ADCS use case, we will use:
auditpol /get /category:*
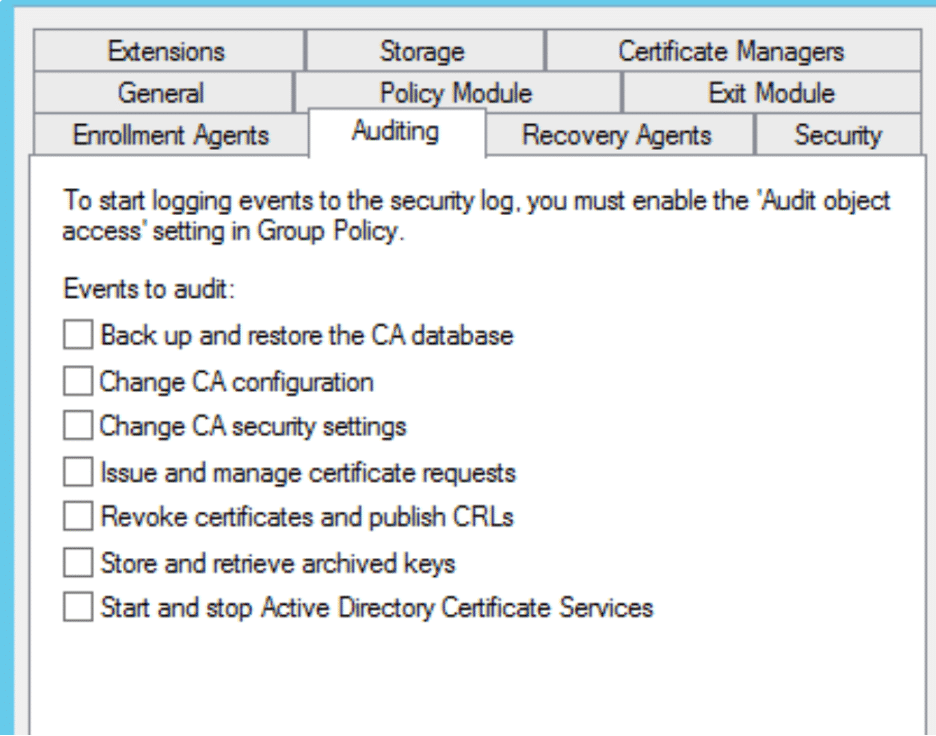
The next step is to enable monitoring using the ADCS snap-in.
To do this, perform the following steps on the ADCS server.
- Open Server Manager
- Select Tools -> Certificate Authority
- Right-click the CA name and select Properties.
- Select monitor
- Enable required monitoring settings
- Backing up and restoring the CA database
- Change CA configuration
- Change CA security settings
- Issuing and managing certificate requests
- Revoke certificates and publish CRLs
- Storing and retrieving archived keys
- Starting and stopping the ADCS
The next step is to enable the certificate template changes using the certutil command.
certutil –setreg policy\EditFlags +EDITF_AUDITCERTTEMPLATELOAD
Some changes can be made directly through the registry, so registry auditing should be enabled. For this, you need to:
- Open regedit on the ADCS server
- Find below the Registry Key
- HKLM\System\CurrentControlSet\Services\CertSvc\Configuration\
- Right click on Configuration and select Permissions
- Click Details
- Select Monitoring and click Add
- Set the principal to Authenticated Users and configure the following permissions:
- set value
- create subkey
- fire extinguishing
- write DAC
- write owner
- read control
Restart the server and see your changes. After rebooting, you will see various event IDs in the security log.

Reboot your server and verify the changes. After the reboot, you should see different event IDs in your Security logs.
Now we have the ADCS auditing up and running.
You can also sieve the audit logs via Azure Arc and Azure Sentinel as well, using “Data Collector Rules” in MS Azure.