We are in an age where digital signature represents the mark of authenticity; seeing the world grow at such a rapid pace today, every single thing needs verification on the internet, be it any source code, script, key pair, or any sort of utility item that a third party offers. All the content we see on the internet needs authenticity before using it. It needs to be checked before it is used, and that mark is provided by Code Signing.
The mark which we are talking about is the main point of attraction of code signing, it is the unique hash value which is calculated before the software code is delivered. Software or utility service is stamped with a digital signature and a hash value to compare whether the received service is from the original author or is tampered with by malicious threat actors.
Now coming to Software supply chain security. The whole, SDLC, software development life cycle’s steps or the activities that interact with applications or otherwise contribute to their development is referred to as the software supply chain
Software supply chain security is the process of protecting the elements, processes, and procedures used in the development and distribution of software that covers developer techniques, development tools, interfaces, third-party and proprietary code, deployment strategies, infrastructure, and interfaces.
These security-related tasks fall under an organization’s purview, as does showing consumers evidence of such efforts.
How can Code Signing help with mitigating Software supply chain attacks?
The main concept of code signing is focused on the integrity of the code, ensuring that the piece of code being delivered to the customer is from the original author. The software’s author signs the code whenever they make changes, ensuring no action is unauthorized.
That means anything being delivered to you comes with a hash released from the author, a key, and a digital certificate to always authenticate first before use.
Code signing is also helpful when working in a team environment. You can use code signing as you exchange source code throughout the SDLC to ensure double authentication, prevent attacks, and even prevent namespace conflicts.
Code signing follows a three-step process
- Creating a unique public-private key
- Hashing
- Decryption and Verification
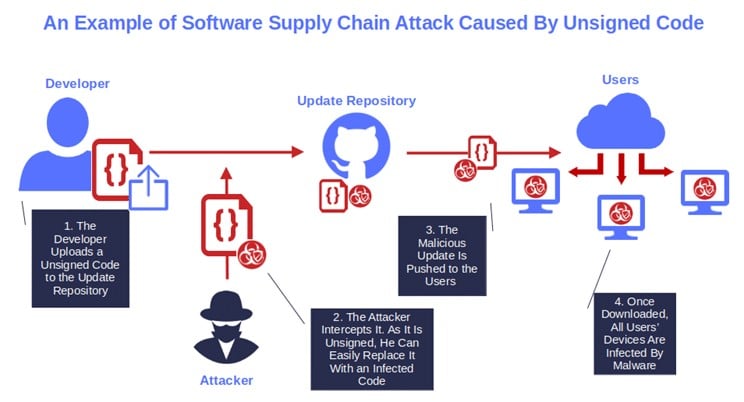
Recent Software Supply Chain Attacks
SolarWinds
Software supply chain threats first gained attention after the SolarWinds hack. Hackers were able to access Orion, the company’s IT monitoring system, which is utilized by over 30,000 businesses, including municipal, state, and federal authorities.
Through an Orion software update, the hackers were able to spread backdoor malware.
So, what happened here?
The malware could not only access system data and function alongside normal SolarWinds operations, evading even antivirus software, but also the hackers could access and impersonate the victims’ accounts and users.
From the time the hackers originally broke into the system in September 2019 until the time the incident was first discovered or reported publicly in December 2020, the perpetrators stayed undetected.
You can see the detailed video explaining the attack on our YouTube channel by following the link below –
Kaseya
IT management software provider Kaseya stated it had been the target of a supply chain assault because of a flaw in its VSA software which hackers took advantage of in July 2021.
The attackers targeted multiple managed service providers (MSPs) and their clients, subsequently identified as REvil, who utilized the vulnerability to launch ransomware operations.
Hackers could access computers via a false update by breaching the VSA server, which is used to distribute a variety of automated IT chores and applications
According to Kaseya, a total of 1,500 firms were impacted by the hack, of which about 60 were its clients.
Later, Kaseya also declared that it hadn’t paid the hacker’s alleged $70 million ($50 million) ransom.
Log4j
Millions of systems were placed in danger by the vulnerability known as Log4Shell that affected Log4j, a Java-based logging application, towards the end of 2021.
Log4j is an open-source program created by the Apache Software Foundation that logs diagnostic data about systems and relays it to users and administrators to keep things operating properly.
However, the Log4Shell vulnerability in December 2021 gave hackers access to networks, allowing them to steal data, discover logins and passwords, and launch other malicious software.
Furthermore, many people and businesses were exposed to attacks due to the widespread use of Log4j.
Log4j vulnerability was given CVE-2021-44832, an RCE vulnerability affecting instances of Log4j 2 in instances where an attacker has permission to modify the logging configuration file and can, in turn, construct a malicious configuration using a JDBC Appender.
CodeSign Secure: A helping hand
Our organization offers a robust and reliable solution- CodeSign secure. Our solution is different because CodeSign Secure helps customers stay ahead of the curve by providing a secure Code Signing solution with tamper-proof storage for the keys and complete visibility and control of Code Signing activities.
Key feature that marks us ahead area: –
- Support for customized workflows of an “M of N” quorum with multi-tier support of approvers
- The command line signing tool provides a faster method to sign requests in bulk.
- Robust access control systems can be integrated with LDAP and customizable workflows to mitigate risks associated with granting wrong access to unauthorized users, allowing them to sign code with malicious certificates.
- Validation of code against up-to-date antivirus definitions for viruses and malware before digitally signing it will mitigate risks associated with signing malicious code.
Conclusion
Code Signing is very crucial for the current day scenarios as piracy and the level of threat posed by the malicious actors to internet is too gigantic and it costs millions of dollars upon the compromise of organisation.
We’re providing a platform for creating/generating, and importing certificates to an organization, documents (env – Windows, Linux, Jar signing, and doc signing) are signed with private key and verified with the respective certificate. Proper and detailed logging feature with an extensive GUI representation (statistical analysis). Management of tools is one of the key advantages of CodeSign Secure.
Prevention is always better than cure, preventing the malicious actors from taking control over personal and client data is always better than disaster recovery. Our organisation helps people with preventing the disaster before it happens.