What is Diffie-Hellman (DH) Key Exchange?
Diffie-Hellman (DH), also known as an exponential key exchange, was published in 1976. DH key exchange is a key exchange protocol that allows the sender and receiver to communicate over a public channel to establish a mutual secret without being transmitted over the internet. DH securely generates a unique session key for encryption and decryption that has the additional property of forward secrecy.
In short, the trick is to use a mathematical function that’s easy to calculate in one direction but very difficult to reverse, even when some of the aspects of the exchange are known.
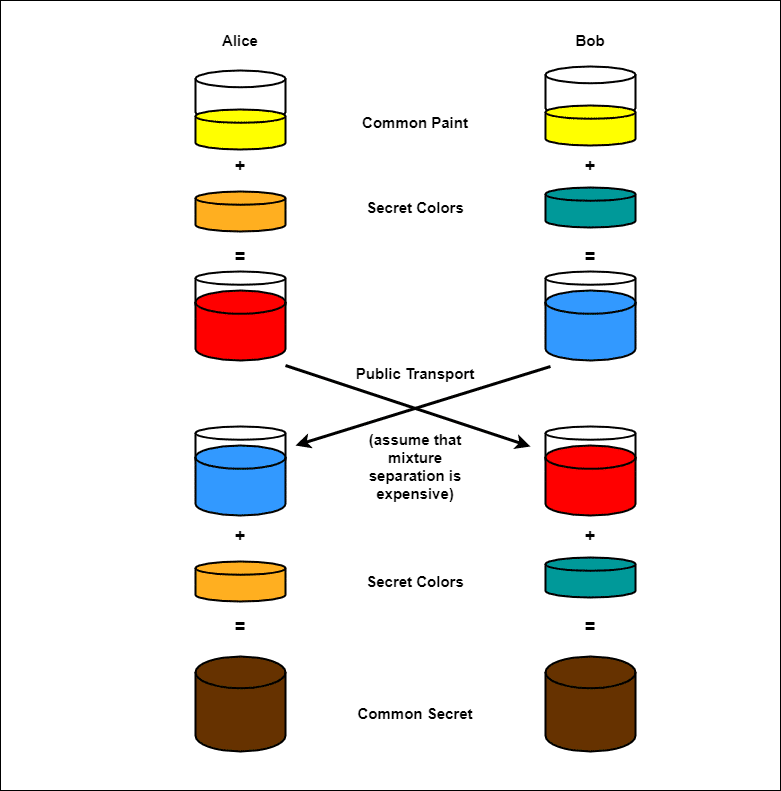
As a typical example with Alice and Bob:
- Let’s say Alice and Bob agreed on a random color, “yellow,” to start with.
- Alice and Bob set a private color for themselves, and they do not let the other party know what color they chose. Let’s assume Alice decides “red” and Bob decides “Aqua.”
- Next, Alice and Bob combine their secret color ( Alice-red; Bob: Aqua) with the “yellow” (“Common color.”)
- Once they have combined the colors, they send the result to the other party. For example, Alice obtains “Sky Blue,” and Bob receives “orange.”
- Once they have received the combined results of their partners, they then add their secret colors to it. For example, Alice adds sky blue to the red, and Bob adds the Aqua to the orange.
- As a result, they both come out with the same color, “Brown.”
The crucial part of the DH key exchange is that both parties end up with the same color without ever sending the common secret across the communication channel. Thus, if an attacker tries to listen to the exchange, it is challenging for the attacker to find the two colors used to get the mixed color (Brown).
Is the Diffie-Hellman Key Exchange Used in Modern Cryptography?
Yes, Diffie-Hellman is used in modern crypto. It is the standard for generating a session key in public. The algorithm has a high processor overhead; it is not used for bulk or stream encryption but rather to create the initial session key for starting the encrypted session. Afterward, under the protection of this session key, other cryptographic protocols negotiate and trade keys for the remainder of the encrypted session. Think of DH as an expensive method of passing that initial secret. More efficient and specialized cryptographic algorithms can protect the confidentiality of the remainder of the session.
Uses of Diffie-Hellman
DH is one of the most popular key exchange protocols. There are various uses of DH to support software and hardware.
- While using DH key exchange, the sender and receiver have no prior knowledge of each other.
- Communication can take place through an insecure channel.
- Public Key Infrastructure (PKI)
- Secure Socket Layer (SSL)
- Transport Layer Security (TLS)
- Secure Shell (SSH)
- Internet Protocol Security (IPsec)
Limitations of Diffie-Hellman
- Does not authenticate either party involved in the exchange.
- It cannot be used for asymmetric exchange.
- It cannot be used to encrypt messages.
- It cannot be used as a digital signature.
What is the RSA Algorithm?
The RSA Algorithm is used to perform public-key cryptography. In the RSA Algorithm, the sender (Bob) encrypts the data to be transferred using his/public key, and the receiver (Alice) decrypts the encrypted data using his/private key.
A typical example of how public key cryptography works?
Public-key cryptography uses two keys, one key to encrypt the data and the other key to decrypt it. The data sender will keep the private secret key and send the public key to all the receivers or recipients of the data. The diagram below shows how public key cryptography works.
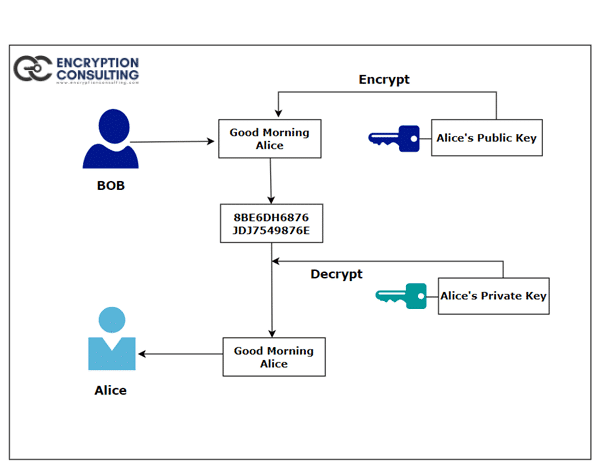
- Bob uses Alice’s public key to encrypt the message and sends it to Alice.
- Alice will use her private key to decrypt the message and get the plaintext.
Uses of RSA
RSA has widely used cryptography in a network environment, and it supports the software and hardware as mentioned below:
- Assures confidentiality, integrity, and authentication of electronic communication.
- Secure electronic communication.
- RSA is used in security protocols such as IPsec, TLS/SSL, and SSH.
- Used for signing a digital signature.
- High-speed and straightforward encryption.
- Easy to implement and understand.
- It prevents the third party from intercepting messages.
Limitations of RSA
- Prolonged key generation.
- Vulnerable when it comes to Key exchange if poorly implemented.
- Slow signing and decryption process.
- RSA doesn’t provide perfect forward secrecy
Diffie-Hellman Key Exchange Vs. RSA
An asymmetric key or public key cryptographic algorithm is far more superior to symmetric key cryptography when the security of confidential data is concerned. The asymmetric key includes many cryptographic algorithms. Both Diffie-Hellman Key Exchange and RSA have advantages and disadvantages. Both algorithms can be modified for better performance. RSA can be mixed with ECC to improve security and performance. DH can be integrated with digital and public key certificates to prevent attacks.
| Parameters | RSA | Diffie-Hellman (DH) Key Exchange |
|---|---|---|
| Public Key encryption algorithm | RSA uses the public-key encryption algorithm. | DH also uses the Public-key encryption algorithm. |
| Purpose | Storage enough for commercial purpose like online shopping. | Storage enough for commercial purposes. |
| Authentication | Assures confidentiality, integrity, and authentication of electronic communication. | Does not authenticate either party involved in the exchange |
| Key Strength | RSA 1024 bits is less robust than Diffie-Hellman. | Diffie-Hellman 1024 bits is much more robust. |
| Attacks | Susceptible to low exponent, typical modulus, and cycle attack. | Sensitive to man in the middle attack. |
| Forward Secrecy | RSA doesn’t provide perfect forward secrecy. | Forward secrecy is in DH key exchange. |
Conclusion
While the Diffie-Hellman key exchange may seem complex, it is fundamental to secure data exchange online. As long as it is implemented alongside an appropriate authentication method and the numbers have been appropriately selected, it is not considered vulnerable to attack. The DH key exchange was an innovative method for helping two unknown parties communicate safely when it was developed in 1976. While we now implement newer versions with larger keys to protect against modern technology, the protocol itself looks like it will continue to be secure until the arrival of quantum computing and the advanced attacks that will come with it.
RSA doesn’t provide perfect forward secrecy, which is another disadvantage compared to the ephemeral Diffie-Hellman key exchange. Collectively, these reasons are why, in many situations, it’s best only to apply RSA in conjunction with the Diffie-Hellman key exchange.
Alternatively, the DH key exchange can be combined with an algorithm like the Digital Signature Standard (DSS) to provide authentication, key exchange, confidentiality, and check the integrity of the data. In such a situation, RSA is not necessary for securing the connection.
The security of both DH and RSA depends on how it is implemented. It isn’t easy to come to a conclusion which one is superior to the other. You will usually prefer RSA over DH and vice versa based on interoperability constraints and depending on the context.
Resources:




