AWS Certificate Manager Private CA


E-commerce businesses are going to be ever more dependent on digital economy and electronic information which enables them to have exacting data privacy compliance and data security framework.
Public Key Infrastructure (PKI) is becoming quintessential to build and map the secure relation between users, devices, services and Organizations to their digital identities in the form of digital signatures and certificates.
To all the crypto engineers out there, have you ever thought of a PKI implementation with minimalistic configuration and a fully scalable feature set comprising of all the benefits which Cloud implementation has to offer?
Welcome to AWS Certificate Manager Private Certificate Authority (ACM PCA). ACM PCA offers almost all the same features provided by On-prem PKI providers.
Let’s understand the PKI offerings from AWS
Enterprises with a secure public website with significant web traffic will prefer this certificate management service which offers auto renewal, multi domain support and a hassle-free certificate management experience.
Note: Kindly note that you can’t export the SSL/TLS public Certificate from the ACM, as the ACM doesn’t allow users to export the private keys of certificates.
Now, let’s discuss the various Two-tier Cloud PKI Models offered by AWS for ACM PCA:
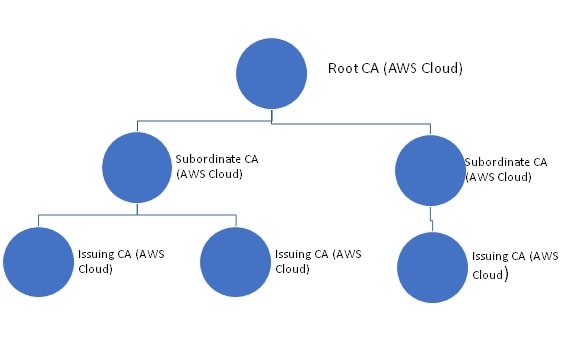
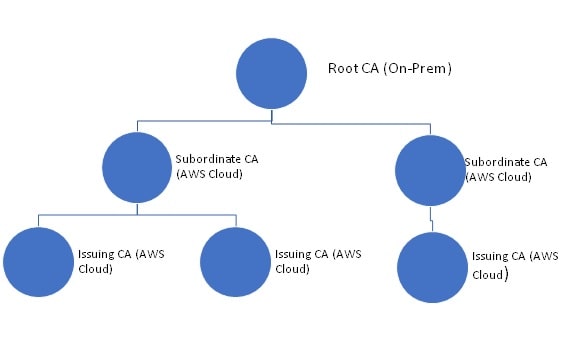
In the Private Cloud architecture, you can host the Root CA or Subordinate CA in the AWS Cloud and use it for all your certificate needs, On-prem as well as Cloud infrastructure. In the Hybrid Cloud architecture, however, you can host the Root CA On-prem and the Subordinate CA in the AWS Cloud for all the certificate requirements of the enterprise.Both these models have their pros and cons. The “Private Cloud Model” provides you all the cloud benefits (high availability, ease of management, access control etc.), but, as a security best practice approach, you might want to have full control over your Root CA with all the cryptographic keys being managed in the On-prem HSM which you don’t have in this approach.On the other hand, the “Hybrid Cloud Model” provides you with complete control over your On-prem Root CA, however, this adds some complexity to the overall architecture by hosting two CAs (Root and Subordinate CA) at different places (On-prem and AWS Cloud).Note: There are various combinations possible for placing the CAs (Root/Policy/Subordinate/Issuing) either in On-prem or Cloud environment/s depending upon the architectural needs of the Organization (like Management of CA lifecycle, DR planning etc.)
With ACM Private CA, you can create a hierarchy of certificate authorities with up to five levels i.e. the root CA, at the top of a hierarchy tree can have as many as four levels of subordinate CAs. You may create multiple hierarchies, each with its own root as well.
The ACM PCA can issue X.509 end-entity certificates for creating encrypted channels, authenticating users, computers, API endpoints, and IoT devices, code signing scenarios and also implementing Online Certificate Status Protocol (OCSP) for obtaining certificate revocation status.
As mentioned, ACM PCA provides X.509 certificates to the end-entity; if AWS Certificate Manager issues a private certificate, the certificate can be associated with any service that is integrated with ACM (e.g. Amazon CloudFront, Elastic Load Balancing, Amazon API Gateway etc.). This is applicable in both scenarios, like the Root CA can be in the AWS Cloud or not, but, the Subordinate CA can only be in the AWS Cloud. Also, if you use the ACM Private CA API or AWS CLI to issue/export a private certificate from ACM, you can install the certificate anywhere depending upon your use-case.
After provisioning the ACM private CA, you can directly issue certificates without having any validation requirement from any third-party CA and as per the customization for your enterprise internal needs. A few of the standard use-cases are:
ACM PCA offers the shared responsibility model for AWS Cloud Security in which “Security of the Cloud” belongs to AWS and “Security in the Cloud” belongs to the “Customer”. This shared security model could be implemented with the help of AWS Data Protection services (e.g. Macie, IAM, Cross Account Access, Logging, Monitoring, Audit Report etc.).
As a final note, I would like to draw your attention to some of the best practices to effectively use ACM PCA:
Quick Note on Pricing
The AWS account is being charged a monthly fee of $400 for each private CA starting from the time that you create it. There is a charge associated with each certificate you issue/export (with its private key) with the model “the more you generate/issue the less you pay”.For the latest ACM Private CA pricing information, see the ACM Pricing page
aws.amazon.com/certificate-manager/pricing/ on the AWS website as prices may vary from time to time.
If you want to secure your data end-to-end with the assurance of legitimate sender source then usage of Public Key Infrastructure (PKI) is must. There are multiple PKI implementations doing the rounds with various complexity levels, however, AWS Certificate Manager Private CA provides this with maximum ease and robust infrastructure providing all the benefits of cloud i.e. pruning maintenance cost, scalability, business continuity, efficiency, flexibility and sec-ops automation.

February 2, 2022

August 20, 2021
July 23, 2021