Your Guide to DORA Compliance


Cybercriminals are hitting financial institutions harder than ever, with cyber threats increasing at an alarming rate. According to IBM, in 2023, the average cost of a data breach in the financial industry was reported to be $5.90 million, and it surged to $6.90 million in 2024. On top of that, a report published by Trend Micro revealed that the banking sector ranked as the No. 1 industry for detected ransomware attacks in 2023. As financial institutions become more interconnected and reliant on digital infrastructure, the risks continue to grow. This evolving threat landscape made it clear that a stronger, standardized approach to cybersecurity and operational resilience is essential. That’s why DORA was introduced.
The Digital Operational Resilience Act (DORA) is a European Union regulation that is designed to strengthen both the operational resilience and regulatory compliance of financial institutions against Information and Communication Technology (ICT) risks. Financial institutions rely heavily on ICT systems for their digital infrastructure, networks, and data management. However, if these systems are not managed effectively, they can become vulnerable entry points for cyber threats, operational failures, and third-party risks. A security breach or operational disruption could expose sensitive data, interrupt critical services, and ultimately jeopardize financial stability.
To avoid this, DORA establishes a comprehensive framework for managing, mitigating, and reporting ICT-related incidents. This framework ensures that financial institutions not only meet regulatory requirements but are also well-equipped to withstand, respond to, and recover from cyber threats and operational disruptions.
DORA provides clear and consistent rules for operational resilience across the EU, primarily focusing on:
DORA applies to a broad range of financial entities, including banks, insurance companies, investment firms, payment service providers, crypto-asset service providers, and ICT service providers that support these financial institutions.
As of January 2025, Article 2 of the DORA regulation specifies the following 21 categories of in-scope entities:
Notably, DORA’s scope extends beyond traditional financial entities to include Information and Communication Technology (ICT) third-party service providers. These are firms that offer digital services to financial institutions, such as cloud service providers, software vendors, data analytics companies, and managed service providers. The inclusion of these service providers highlights the critical role they play in the infrastructure of the financial sector and the risks that come with dependency on them.
Under DORA, ICT third-party service providers must:
By encompassing both financial institutions and their critical ICT service providers, DORA aims to create a strong and unified approach to operational resilience across the EU’s financial sector.
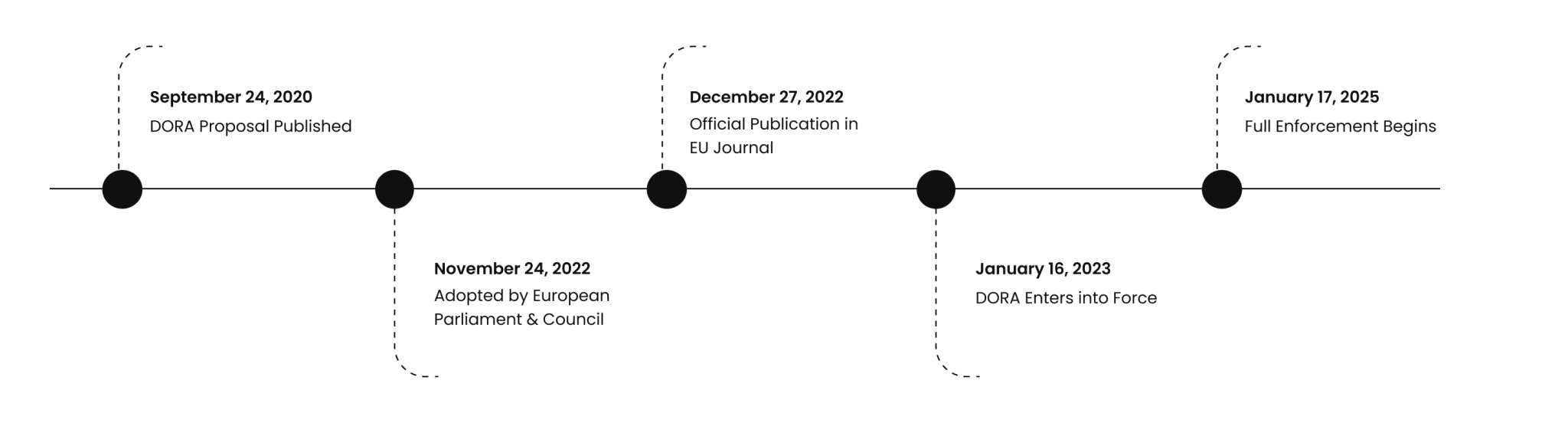
DORA was first proposed on September 24, 2020, and later approved by the European Parliament and Council on November 24, 2022. It was officially published in the EU Journal on December 27, 2022, and came into effect on January 16, 2023. Financial entities and third-party service providers were given two years to familiarize themselves with DORA’s requirements and achieve compliance before full enforcement began on January 17, 2025.
Now that the deadline has passed, organizations must ensure that they are fully compliant with DORA’s requirements, conduct regular resilience testing, and continuously monitor their ICT risk management frameworks to avoid penalties and operational disruptions.
DORA is built on five key pillars that strengthen the digital resilience of financial institutions, and they are:
ICT Risk Management
As outlined in Chapter II, ICT Risk Management is a fundamental pillar of DORA. It ensures that financial entities take a structured and proactive approach to identify, assess, and mitigate technology-related risks. By enforcing continuous monitoring, timely risk assessments, and adaptive response strategies, DORA enhances resilience against cyber threats and operational disruptions.
Financial institutions must implement the following measures to enhance ICT risk management:
ICT-Related Incident Reporting
Chapter III, ICT-related incident management, classification, and reporting, lays out a standardized approach for detecting, classifying, and reporting ICT incidents, ensuring financial institutions stay ahead of potential threats.
Under DORA, financial entities need structured processes to track incidents, assess their impact, and notify the right people—both internally and externally. Internally, that means quickly identifying issues and keeping all relevant teams updated. Externally, it involves timely reporting to regulators and, in cases like data breaches, notifying affected customers.
To comply with DORA, financial institutions must adhere to the following guidelines:
Digital Operational Resilience Testing
DORA mandates that financial institutions regularly test their ICT risk management frameworks to assess their ability to withstand cyber threats and operational disruptions. According to Chapter IV – Digital Operational Resilience Testing, financial entities must perform regular risk-based testing, including vulnerability assessments and scenario-based testing, to identify weaknesses and implement corrective measures. These tests must be conducted by independent internal or external parties.
To strengthen digital resilience, financial institutions must take the following actions:
Management of ICT Third-Party Risk
DORA imposes strict requirements on financial institutions to manage risks associated with ICT service providers, with Chapter V specifically focusing on ICT third-party risk management. It ensures that financial entities thoroughly assess third-party providers before entering agreements, ensuring they meet security and regulatory compliance. Contracts must clearly define service scope, quality expectations, monitoring requirements, and termination clauses.
To comply with DORA, financial institutions must implement the following measures:
Information and Intelligence Sharing
Chapter VI promotes the sharing of information and threat intelligence amongst the EU financial community. By fostering collaboration, financial institutions can enhance awareness, strengthen threat detection, and build more effective defense strategies against cyber risks.
To ensure secure and effective information sharing, financial institutions must adhere to the following guidelines:
Together, these five pillars create a strong foundation for financial institutions to navigate ICT risks, ensuring resilience against cyber threats and operational disruptions. By emphasizing proactive risk management, continuous testing, and secure collaboration, DORA enhances the financial sector’s ability to safeguard critical operations and maintain regulatory compliance.
Cryptography plays a fundamental role in the Digital Operational Resilience Act (DORA) by protecting the digital infrastructure, data, and communication systems of financial institutions. As the financial sector becomes more dependent on Information and Communication Technology (ICT), the importance of cryptographic measures in ensuring the confidentiality, integrity, and availability of critical data cannot be overstated. DORA outlines specific obligations related to cryptographic controls to mitigate risks associated with cybersecurity threats and operational disruptions.
Article 6 – Encryption and Cryptographic Controls
DORA mandates that financial institutions establish a formal policy for encryption and cryptographic controls to protect financial and customer data. This includes:
Proper management of cryptographic keys is critical for preventing unauthorized access, data breaches, and operational risks. DORA requires financial institutions to:
DORA reinforces the need for secure authentication methods and controlled access to ICT assets using cryptographic security measures. Financial institutions must:
Failing to comply with DORA isn’t just a regulatory issue—it comes with serious financial and reputational risks. Financial institutions and third-party service providers (TPSPs) that don’t meet DORA’s requirements can face hefty fines and other penalties.
Here’s what non-compliance could mean:
For Financial Entities:
For Third-Party Service Providers (TPSPs):
Organizations that fail to meet the requirements of DORA not only face significant penalties but also risk damaging their reputation and losing customer trust.
DORA will be enforced by various EU regulatory bodies. National Competent Authorities (NCAs) in each EU member state will play a key role in overseeing compliance at a local level.
At the European level, three major regulatory agencies will be involved:
These regulators will have the authority to oversee and enforce compliance with DORA, ensuring that financial entities meet the required resilience obligations. They can conduct audits and inspections to assess adherence, impose fines and penalties on organizations that fail to comply, and directly monitor ICT third-party service providers to ensure they implement the necessary risk management, security, and operational resilience measures as required by DORA.
At Encryption Consulting (EC), we specialize in providing tailored encryption assessments to help organizations achieve compliance with regulatory requirements such as DORA, HIPAA, and GDPR, as well as industry standards like NIST and PCI-DSS. Our process begins with evaluating your current infrastructure against established standards, allowing us to identify any gaps in your security measures. From there, we provide a roadmap that outlines the steps needed to achieve compliance effectively. Here’s how we can assist you:
We start with a review of your existing policies. This involves identifying your current encryption capabilities and understanding any limitations in your systems. We also examine your overall security setup to ensure we have a complete picture of your environment, taking into account various use cases relevant to your organization.
Next, we assess the gaps in your current policies. This includes identifying gaps in your existing policies against industry standards to ensure adherence to security and compliance requirements. We also conduct workshops to facilitate discussions about your current applications, encouraging collaboration among team members to gather valuable insights. Additionally, we create an assessment questionnaire designed to capture important information about your encryption practices. Through this evaluation, we identify existing data encryption capabilities and pinpoint specific areas for improvement.
Once the assessment is complete, we transition into the implementation phase with a detailed roadmap. We provide a comprehensive report summarizing our findings and recommendations for each finding. This report serves as a foundational guide for implementing necessary encryption enhancements. Our roadmap aligns your processes with industry standards, strengthens data security, and ensures compliance.
By choosing our encryption assessment services, you take a proactive step towards strengthening your organization’s compliance with relevant standards. We guide you through the process, ensuring your strategies are both effective and aligned with your business goals.
Digital operational resilience is no longer an option; it has become a necessity, and that is why DORA was introduced. It outlines a clear framework for managing ICT risks, enhancing incident response, and securing third-party dependencies. Effective ICT risk management, proactive incident response, and rigorous resilience testing are not just about regulatory compliance—they are essential for maintaining stability in an increasingly digital world. By integrating DORA’s principles into daily operations, firms can strengthen their defenses, protect customer trust, and stay ahead of evolving threats.

April 3, 2025

July 3, 2024

June 6, 2024