Code Signing, Education Center
What is CSP and PKCS#11?

Code Signing, Education Center

CSP (Cryptographic Service Provider) and PKCS#11 (Public-Key Cryptography Standard #11) are both cryptographic frameworks that enable secure access to cryptographic functions and devices. A CSP (Cryptographic Service Provider) is software that helps applications encrypt data and manage keys securely, while PKCS#11 is a standard that allows software to interact with hardware devices like smart cards or security modules for secure tasks like encryption and key storage.
We live in a world where nothing is more important than data security. There are always chances and risks for data leaks and altering of data. So, we use cryptography and cybersecurity to keep data secure. While we are discussing the topic, CSP and PKCS#11 must be addressed. Let us take an example and understand.
Imagine a financial company handling hundreds of transactions every minute. Each transaction involves sensitive information like bank account details. To keep this data safe, CSPs are used to encrypt information before sending it over the internet. PKCS#11 helps by securely storing the encryption keys in hardware devices, like security cards or modules, ensuring that only authorized people can access the keys. This way, every transaction is protected and meets security rules.
Let’s start with CSP (Cryptographic Service Provider). In Microsoft Windows, a CSP is a software library that provides implementations for the Microsoft CryptoAPI (CAPI).
CSPs are part of Windows’ system and are responsible for providing the tools and support that applications need to perform encryption along with decryption. When a program calls CryptoAPI functions, they are redirected to the CSPs, which manage the cryptographic algorithms and security standards. CSPs are special DLLs (Dynamic Link Libraries) that must be digitally signed by Microsoft. Windows checks the signature when loading a CSP and re-scans it periodically to ensure it’s not tampered with. Non-Microsoft developers need to follow legal procedures to get their CSPs signed, but for testing, they can configure Windows to recognize their own signatures.
They are used for other cryptographic operations as well. Sometimes, you see an icon like a padlock next to the website you are working on. That is encryption working for you.
When you visit a secure website, like an online shopping site, you often see a small padlock icon next to the website’s address. This means that encryption is working to protect your information. For example, when you enter your credit card details, CSPs (Cryptographic Service Providers) encrypt that information so it can’t be read by anyone else while it’s traveling over the internet. This keeps your data safe from attackers.
Now that we understand what a CSP is, let us learn about why they are so important.
A CSP is an essential component that helps manage encryption and security in a seamless way. It simplifies how applications handle sensitive data, making them secure without requiring developers to dive into the complexities of cryptography. Let’s explore why CSPs are so important.
| Provider | Description | Crypto | Use Cases | Key Features |
| Microsoft Software Key Storage Provider (KSP) | General-purpose software-based provider for securely storing and accessing cryptographic keys. | RSA ECC SHA1 SHA2 | General cryptographic operations like key exchange, digital signatures, and data encryption. | It supports modern algorithms, is highly compatible with applications, and is software-based (no special hardware required). |
| Microsoft Smart Card Key Storage Provider | Manages cryptographic keys stored on smart cards. | RSA ECC SHA1 SHA2 | Secure logins, identity verification, and multi-factor authentication using smart cards. | Ensures private keys stay on the card; physical security through hardware-based storage. |
| Microsoft Platform Crypto Provider | Leverages Trusted Platform Module (TPM) for hardware-backed cryptographic operations. | RSA ECC SHA1 SHA2 | Secure boot, disk encryption, and hardware-backed key storage for enhanced security. | Hardware-based protection; key attestation; prevents software-based key theft. |
| Microsoft Enhanced Cryptographic Provider | An enhanced version of the base cryptographic provider offers stronger security with support for longer keys. | RSA, AES, SHA | Applications requiring longer key lengths or backward compatibility for enhanced security. | Backward compatible with legacy systems; supports modern encryption standards. |
| Microsoft AES Cryptographic Provider | Focused on providing robust encryption using the Advanced Encryption Standard (AES). | AES | Applications that need strong symmetric encryption, such as file or data encryption. | Dedicated to AES and optimized for fast and secure encryption. |
Other than the providers mentioned above, there are also many other cryptographic service providers (CSPs) currently available from Microsoft. It has several legacy and deprecated cryptographic providers that have been replaced by modern solutions due to advancements in security requirements. The Microsoft Base Cryptographic Provider was one of the earliest providers, supporting basic algorithms like RSA and SHA1. However, it is now outdated and unsuitable for strong encryption needs. Similarly, the Microsoft Base DSS and Diffie-Hellman Cryptographic Provider, which handled digital signatures and key exchange, and its enhanced version, Microsoft Enhanced DSS and Diffie-Hellman Provider, have been replaced by modern providers that support stronger algorithms like ECC.
The Microsoft RSA SChannel Cryptographic Provider was used for SSL/TLS communications but is now considered outdated due to improvements in TLS protocols and encryption standards. Additionally, the Microsoft Enhanced RSA and AES Provider, which supported AES and longer RSA keys, has also been deprecated in favor of more optimized and secure options.
Modern cryptographic providers, such as the Microsoft Software Key Storage Provider and Microsoft Platform Crypto Provider, now offer robust encryption, support stronger algorithms, and ensure compliance with standards like PCI DSS, HIPAA, and GDPR. Developers are encouraged to adopt these modern providers to ensure their applications remain secure and meet current regulatory requirements.
For more details, visit the official documentation: Microsoft Cryptographic Providers.
PKCS#11 is more diverse and versatile than a CSP. It stands for Public-Key Cryptography Standard #11. PKCS is a set of cryptographic standards developed by RSA Laboratories, and each number in the series (like #1, #7, #12, etc.) defines a specific standard related to public-key cryptography. Knowing all of this, the real question that arises is, what exactly does PKCS#11 do? It is the standard among various others that defines a cryptographic token interface. This standard allows applications to communicate with cryptographic hardware devices such as USB tokens, smart cards, and even HSMs.
Consider for a moment that your company uses a smart card to securely store employee ID keys for system access. When you swipe your card, PKCS#11, through its Cryptoki API, communicates with the smart card (acting as a token) to verify your identity. Instead of exposing your key, the token securely processes it within the smart card, and Cryptoki simply sends back a confirmation that you’re authorized.
In short, PKCS#11 and Cryptoki let your software work with secure devices like smart cards or HSMs while keeping sensitive data locked inside the hardware.
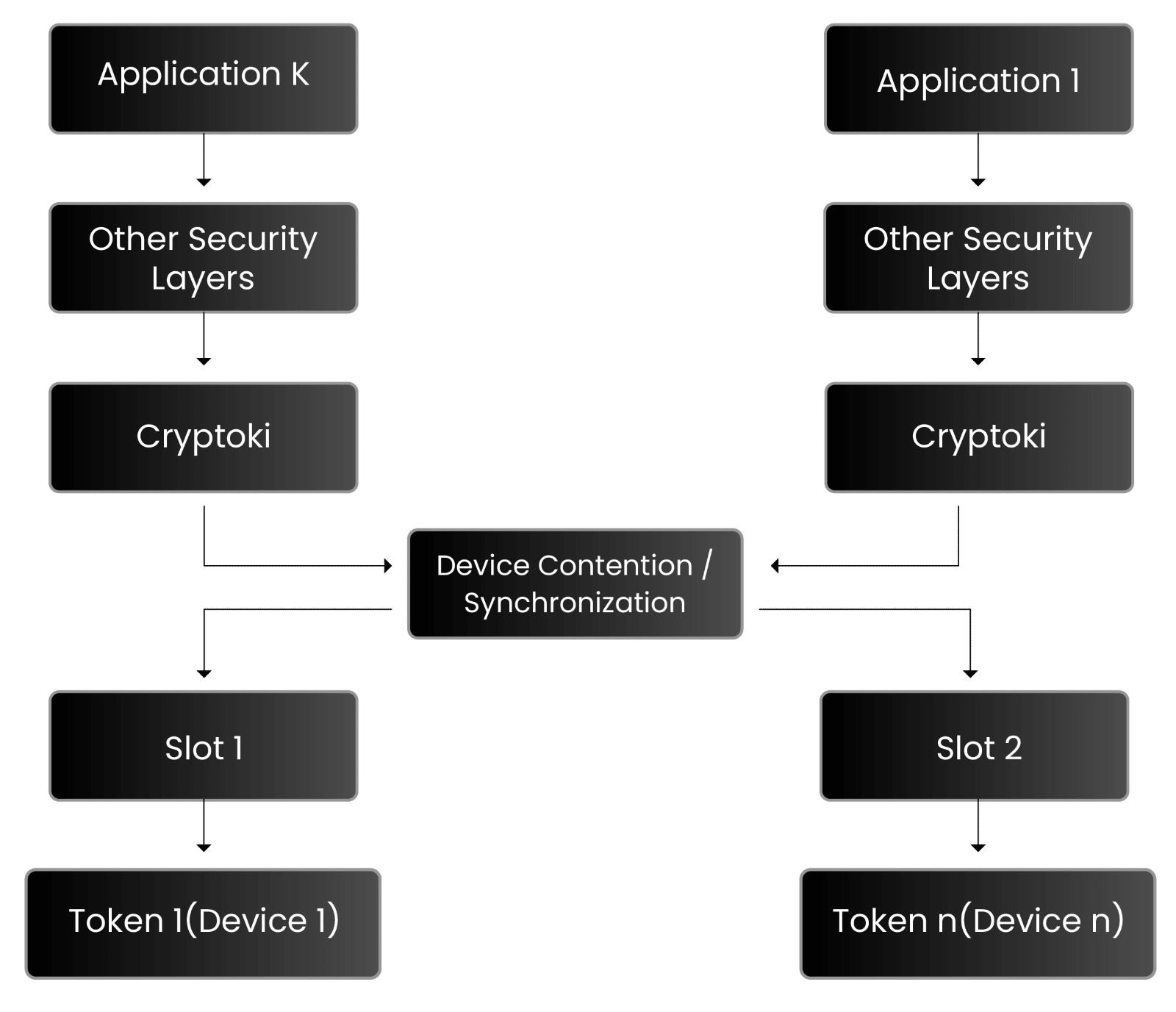
This architecture explains how cryptographic hardware tokens are accessed for secure key storage and digital signatures. At its core, Cryptoki is a standardized interface that allows applications, like web browsers or email clients, to interact with the token. Additional security layers, such as authentication and access control, ensure that only authorized applications can access the token.
The device contention and synchronization layer manage simultaneous access requests, while the “slot” represents the location where the token is accessed. The token itself stores cryptographic keys and performs operations. Compliance with standards like FIPS 140-2 ensures the system meets security requirements, with Cryptoki acting as the set of instructions to access the token safely.
Let us look at PKCS#11 in more detail. It serves as a low-level interface for performing cryptographic operations, allowing applications to interact with hardware devices without needing to communicate through the device’s drivers directly.
In this model, a slot represents the physical device interface, like a smart card reader, while the token is the actual device, such as the smart card. It’s also possible for multiple slots to share the same token, depending on the system.
Since we are talking about PKCS#11, let us clear up the confusion between slots, tokens, and objects.
A slot in PKCS#11 refers to a physical interface through which the application interacts with the cryptographic token. Think of a slot like the port of a USB stick or a smart card reader. It’s the entry point to access a token. A slot is where you “plug in” a token, which could be a smart card, USB security key, or another type of hardware device. A single system can have multiple slots, and in some cases, the same token (like a smart card) can be used across different slots, allowing flexibility in how the hardware is accessed.
The token itself is the physical device that stores cryptographic objects and carries out cryptographic operations. This is the heart of PKCS#11. Tokens can be anything from smart cards and USB keys to more complex hardware security modules (HSMs). The token securely stores objects like keys and certificates and performs tasks such as encryption, decryption, signing, and authentication. The data inside the token is protected by strict access controls, ensuring that only authorized users or applications can interact with it.
Objects are the data entities managed by the token to perform cryptographic functions, and they can range from encryption keys to certificates or even custom data objects defined by the manufacturer. One type of object is a Data Object, which can include anything the application needs to store, such as files or application-specific data. These objects are flexible and can vary depending on the requirements of the application.
Another type of object is a Certificate Object. These are used for identification and security. Digital certificates, such as X.509 certificates, are stored as certificate objects. They prove that an entity (like a website or user) is who it claims to be, helping to establish trust.
Key objects are the most critical in cryptographic operations. Keys can be public, private, or secret keys. Public keys encrypt data or verify digital signatures, private keys decrypt data or sign messages, and then there are secret keys (symmetric keys) that are used for both encrypting and decrypting data.
There is one more category called Vendor Defined Objects. These are custom objects created by the token manufacturer. They are used to store special information or handle unique features of the token, such as custom algorithms or proprietary data formats.
When an application wants to perform a cryptographic function, it interacts with a token through a slot. The token, in turn, manages the objects that are required to perform tasks like encryption or signing. For example, if an application needs to encrypt data, it will communicate with a token using a slot, which in turn will ask the token to use a specific key object. The token will then retrieve a key and perform the encryption function, all while keeping the key secure within the token. Similarly, if the application needs to verify a certificate, the token can provide the certificate object stored inside.
Session and Access control in PKCS#11
In PKCS#11, access to a token’s objects is managed through sessions and permissions. A session is a temporary connection between an application and a token, active only while it’s open. Objects on a token can be public or private. Public objects are accessible to anyone, while private objects require the user to log in to the token. There are two types of users: Security Officers (SOs), who manage the token and set up PINs, and normal users, who log in to access their private objects.
PKCS#11 streamlines secure communication between applications and cryptographic hardware, making it easier to protect sensitive data across different platforms. This is essential for ensuring strong security in protecting data.
Standards: PKCS#11 provides a unified standard for communication between applications and cryptographic devices. It ensures that different applications can interact with cryptographic hardware in a consistent way, regardless of the device manufacturer. This standardization improves compatibility and reliability.
Cross-platform Usage: PKCS#11 is designed to work across multiple operating systems, including Windows, Linux, and macOS. Its platform independence allows developers to implement cryptographic functions in applications without worrying about the underlying system, offering greater flexibility and ease of use.
Secure Key Storage: PKCS#11 enables the secure storage of private keys, which are essential for tasks like signing, on hardware tokens. By keeping the keys on physical devices, it prevents unauthorized access and theft, ensuring that sensitive cryptographic operations remain protected.
Compliances: PKCS#11 adheres to industry standards such as FIPS 140-2, which is required for secure key management. This compliance ensures that cryptographic hardware and software meet strict security requirements, making them suitable for high-security applications.
For more detailed information on FIPS 140-2 compliance and its relevance to PKCS#11, you can refer to the official NIST documentation:
| Features | CSP | PKCS#11 |
| Platform | Windows-specific | Cross-platform (Windows, Linux, macOS) |
| Primary Use | Mainly for Windows applications | Any application interacting with cryptographic tokens |
| Hardware Support | Smart Cards, HSMs, Software | Smart Cards, HSMs, USB Tokens |
| Standardization | Microsoft-specific interface | Open standard (RSA Security) |
| Flexibility | Tied to Windows environment | Works across multiple operating systems |
| Key Management | Integrated with Windows security | Secure key storage in hardware tokens |
| Cryptographic Operations | Basic operations in Windows apps | Supports a wide range of cryptographic functions |
| Usage in Code Signing | Limited to Windows apps | Essential for secure key management in code signing across platforms |
Why exactly should you care about CSP vs PKCS#11? Think of a healthcare organization that stores patient records online. Now, each time anyone accesses the patient’s information, it must be encrypted. This is the point where the CSP comes into play; it manages your sensitive data for your security during the transmissions. Even if somehow a bad hacker intercepts the data, what he receives is gibberish, all thanks to the CSP’s efforts.
If you are still wondering about PKCS#11, think of it this way. Healthcare professionals use smart devices to store their credentials. Here, PKCS#11 ensures that only authorized staff members can access the data of any patient. The way it works is cryptographic keys are securely stored and protected from any unauthorized access.
Encryption Consulting specializes in enhancing cryptographic security with tailored services. We provide seamless PKCS#11 integration, enabling secure communication between your applications and cryptographic hardware like HSMs and smart cards. Our CodeSign Secure solutions offer robust code signing, utilizing Entrust nShield HSMs to ensure tamper-resistant key management and compliance with FIPS 140-2 standards. Additionally, we offer secure XML document signing with PKCS#11 to maintain data integrity and authenticity. To empower your team, we provide comprehensive training programs, ensuring your cryptographic systems are secure, compliant, and optimized. We also provide a Certificate Lifecycle Management product to enhance the security of your organization.
As cyber threats grow day by day, using the correct tools like CSP and PKCS to protect our data is crucial. CSP streamlines security for Windows apps, while PKCS#11 enhances security across various platforms, including Mac and Linux. Understanding CSP and PKCS is essential for anyone involved in data security. These standards make it easier to manage cryptographic operations and keep sensitive information safe, whether you’re developing Windows applications or working across different platforms.
Furthermore, both CSP and PKCS provide reliable frameworks for secure key management, essential for protecting sensitive data in sectors such as finance, healthcare, and government. As industries increasingly rely on digital solutions, these cryptographic standards ensure that data integrity and confidentiality remain intact. Adopting CSP and PKCS can help organizations comply with strict regulatory requirements while mitigating the risk of unauthorized access, and any other possible risks.