Certificate Lifecycle Management
X.509 certifications for protection malicious network impersonators

Certificate Lifecycle Management

An X.509 certificate is a digital certificate that defines the format of Public Key Infrastructure (PKI) certificates and provides safety against malicious network impersonators. Man-in-the-middle attacks can be easily initiated without x.509 authentication.
It is widely used for many internet protocols including SSL/TLS connections that are secure protocols for browsing the web. An X.509 certificate, which is either signed by a trusted certificate authority or self-signed, contains a public key as well as the identification of a hostname, company, or individual. It is also used in offline applications such as electronic signatures.
X.509 also defines certificate revocation lists, which is a way to distribute information about certificates that have been declared invalid by a signing authority as well as by a certification path validation algorithm.
A digital certificate is indeed a file or an encrypted password that confirms the authenticity of a device, server, or user by utilizing PKI and cryptography.
Organizations can employ digital certificate authentication to ensure that only trustworthy devices and users can connect to their networks. Another frequent application for digital certificates is to verify the legitimacy of a website to a web browser, often known as a secure sockets layer or SSL certificate.
A digital certificate contains identifying information such as a user’s identity, company, or department, as well as the Internet Protocol (IP) address or the serial number of a device. Digital certificates contain a copy of the certificate holder’s public key, which must be matched to a matching private key to be valid.
X.509 certificates have several beneficial properties that passwords don’t have. They prove to be advantageous over normal passwords.
The Abstract Syntax Notation One (ASN.1) is the basis for X.509 standards. Using ASN, the X.509 certificate format uses a related public and private key pair to encrypt and decrypt a message.
The CA issues an X.509 certificate to an entity, and that certificate is attached to it like a photo ID badge. Unlike insecure passwords, they cannot be lost or stolen. Using the badge analogy, you can easily imagine how authentication works: the certificate is “flashed” like an ID at the resource requiring authentication.
A PKI contains a string of randomly generated numbers that can be used to encrypt a message. Only the selected recipient can decrypt and read this encrypted message and can only be deciphered and read by using the associated private key, which is also made of a long string of random numbers.
This private key is kept private and is only known to the recipient. As the public key is published for all the world to see, a complex cryptographic algorithm that generates random numeric combinations of varying lengths is used to create a public key and pair them with an associated private key.
The following are the most often used algorithms for generating public keys:
Each certificate has several attributes and fields that contain information about the user, the issuer, and the cryptographic parameters of the certificate itself.
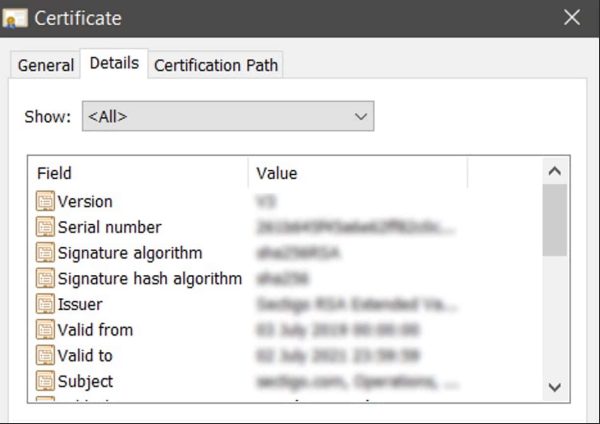
Version
The X.509 version is associated with the certificate.
Serial number
The unique serial number assigned by the CA to each issued certificate.
Algorithm information
The cryptographic algorithm or a private key algorithm, usually RSA 2048.
Issuer name
The issuing CA’s name
Validity period
The period in which the certificate will be considered valid.
Subject distinguished name
The name of the device that the certificate is being issued to.
Subject public key information
The public key linked to the identity.
Many internet protocols rely on X.509, and PKI technology is used in a variety of applications every day, including Web server security, digital signatures, document signing, and digital identities.
PKI serves as the foundation for the secure sockets layer (SSL) and transport layer security (TLS) protocols, which underpin HTTPS secure browser connections. Without SSL certificates or TLS to create secure connections, attackers might intercept communications and read their contents through the Internet or other IP networks using a variety of attack vectors, such as man-in-the-middle assaults.
PKI-based certificates may be used for digital signatures and document signing in addition to securing messaging.
Digital signatures are a sort of electronic signature that uses PKI to validate the signer’s identity as well as the integrity of the signature and the document. Because digital signatures are generated by producing a hash, which is encrypted using the sender’s private key, they cannot be manipulated or reproduced in any manner.
This cryptographic verification mathematically connects the signature to the original message to verify that the sender has been verified and that the message has not been changed.
Code Signing enables application creators to provide a layer of confidence by digitally signing apps, drivers, and software programs, allowing end-users to verify that the code they get has not been altered or compromised by a third party. These digital certificates feature the software developer’s signature, the firm name, and timestamping to ensure the code is secure and trustworthy.
Client-Certificate Authentication is a mutual certificate-based authentication in which users provide digital certificates compliant with the X.509 standards to the servers as a component of the TLS protocol handshake to prove their identities; this is also recognized as mutual or two-way TLS authentication.
While TLS’s principal role on the Internet is to support encryption and trust, enabling a web browser to validate the authenticity of the website, the protocol also works in reverse, with X.509 client certificates used to authenticate a client to the webserver.
One of the most important components of X.509 certificates is their effective management at scale through automation. Companies that do not have outstanding people, procedures, and technology in place expose themselves to security breaches, outages, brand harm, and critical infrastructure failures.
X.509 certificates are key assets to build and maintain digital trust in the digital world. If these certificates are not effectively managed, companies can be at risk of breaches and failed audits.
Take a list of your existing X.509 certificate management capabilities with us at Encryption Consulting and determine whether a new solution is necessary to keep up with the constant growth of your digital certificates.