A Detailed Guide on Building your own PKI


With the ever-changing and expanding enterprise infrastructure, it has become extremely important that every organization have their own robust and mature Public Key Infrastructure (PKI) set up that can establish trust between their systems, applications, users, and devices on untrusted networks. The adoption of private cloud, public cloud, DevOps, microservices, and the addition of IOT and network connected devices presents a wide range of areas to protect. A Public Key Infrastructure not only provides trusted identities to users and devices, but also provides a secure channel to protect communications in-transit.
Today, most PKI setups in organizations are decades old and need to be revamped and upgraded to match the changing IT landscape. The biggest need for most organizations is to provide a highly secure and very robust PKI setup that can issue and manage digital certificates quickly through self-provisioned systems. An internal PKI setup by the organization should also support both on-premises and Cloud systems, to meet DevOps requirements. But how does a PKI work?
A PKI is a setup that provides digital certificates to end-users, systems, devices, and applications to provide them with trusted identities. These identities are used for authentication of the certificate holder, as well as for establishing secure communications to other certificate holders within the network. A PKI infrastructure is based upon asymmetric key cryptography utilizing a public key and private key pair associated with a digital certificate issued by an Issuing Certificate Authority (CA). This certificate authority establishes trust between two certificate holders with the help of these digital certificates. Along with providing the certificate holders with their identity, these certificates also provide access rights and enables the certificate holder to establish a secure channel between two certificate holders to communicate.
A digital certificate contains the following information to prove the identity of the certificate holder:
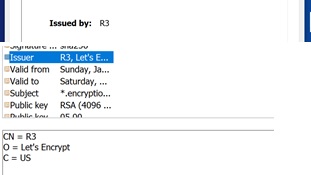
Details of Certificate Issuer: The Issuer details include the name of the Issuing CA, shown on the General tab under the “Issued by” field and in the Details tab under the “Issuer” field. The “Issuer” field not only shows the name of the Issuing CA, but also the Common Name, Organization name, and Country of the the Issuer.
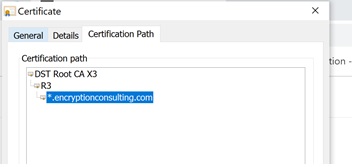
Certification Path: Also included in a digital certificate is the certification path of the certificate. This helps other users, applications, or devices within the network verify the validity of the certificate.
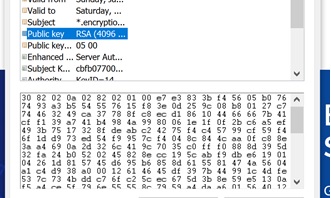
Public key: As mentioned, the certificate holders public key is stored within the certificate. This, along with their own private key, verifies that the key holder matches the public key within the certificate.
Key usage & extended key usage: The “Key Usage” field tells the viewer what the key is used for. There is also a chance that the certificate has an “Extended Key Usage” field, which tells of other uses for the key, that is not included in the “Key Usage” field.

Digital signature of the issuer: One other important part of a digital certificate is the issuer’s digital signature. This helps with verification of the certificate, as it lets the viewer know who issued the certificate.

The “Key Usage” field can offer a lot of different uses for the digital certificate. The following are some of the most common usages for certificates:
The two most common PKI architectures are the two-tier and three-tier architecture. Below are the PKI components that make up each type of PKI architecture:
A two-tier architecture is the most common form of PKI hierarchy, and also the most balanced architecture. It involves only a Root CA and the Issuing CAs in the PKI. This format makes it simple to deploy a two-tier PKI, without losing the security of the PKI. The below image shows how the setup of a two-tier PKI looks.
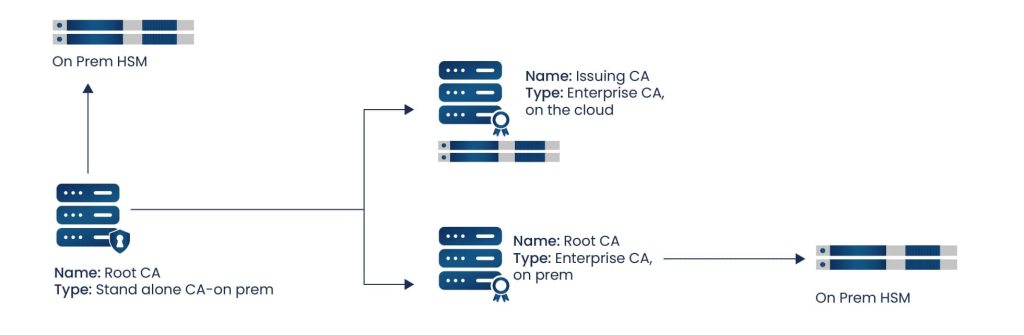
The design of a two-tier PKI architecture works with security and simplicity in mind, allowing the root of trust, the Root CA, to stay offline, protecting it from attack. Since the Root CA cannot be compromised, there is no worry that certificates are being misused or given to untrusted users. Instead of the Root CA giving out certificates, it creates the certificates for its original Issuing CAs, and allows them to to issue certificates to end-users. Two-tier PKI architectures are the most common type of hierarchy used.

The three-tier architecture is the most secure, as there are more links in the chain that would need to be compromised by attackers. However, setting up a three-tier architecture is a much more complicated process than setting up a two-tier architecture. With Intermediate CAs added into the mix, there are many more CAs to set up and integrate within the PKI, especially if a large number of Issuing and Intermediate CAs need to be created. The more CAs needed in a PKI, the more complicated implementation and maintainence is. A three-tier architecture is used much less often than a two-tier architecture.
One form of PKI becoming more and more common is PKI as a Service. The way PKI as a Service works is that a provider will have the PKI setup, whether at their own data center or within your organization, and handle all of the management and updating in the PKI. This allows the organizations purchasing this service to not need to train or hire PKI professionals, thus saving them money and manpower. If the PKI is setup at the provider’s data center, the organization purchasing their services will most likely have the PKI issue certificates to their users, without having their own Issuing CA. PKI as a Service is one of the many services provided by Encryption Consulting. We assist your organization in the design, implementation, and deployment of your PKI. Part of our PKI setup includes the use of an on-premises Thales-SafeNet, nCipher, or Utimaco HSM. We can implement it in our data center in Dallas, Texas, or onto your site. Whichever hardware security module you choose to use, they are all FIPS 140-2 Level 2 and 3 compliant, so you should reach all of your compliance requirements. Along with an HSM, we also help you build and design a backup for your PKI, for minimal to no loss of service from unseen circumstances. We can also implement different SIEM tools into your PKI, allowing you to monitor certificates and keys, to keep you up to date on revoked certificates, unused keys, etc. Our PKI as a Service can also be set up either on-premises or on the Cloud.


February 21, 2025

October 9, 2024